For many years, encryption was seen as a silver bullet – simply turn it on and become instantly compliant, with data magically secured. In the last few years however, organizations have become increasingly aware that the first step to effective data protection is defining which type of data you need to protect, and where it is vulnerable. It is this understanding that is driving the need for companies to adopt an enterprise data protection strategy, rather than viewing encryption as a series of point solutions.
The 2012 Global Encryption Trends Study, an annual independent research report by the Ponemon Institute and sponsored by Thales (News - Alert), reveals that for the first time, the majority of companies now have a formal encryption strategy applied consistently across the enterprise.
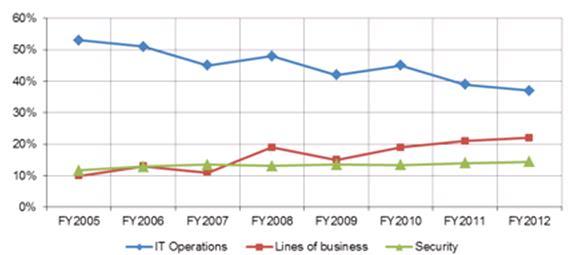
The focus on encryption as a strategic business issue is further evidenced by the fact that non-IT business leaders are steadily becoming more influential in determining a company’s encryption strategy. For the first time, in the United States, business managers have now become the most influential group in setting the encryption strategy, overtaking the IT and security teams. On top of this, the percentage of IT budget allocated to encryption continues to grow, nearly doubling from 10%-18% since the annual study began in 2005.
Perceived threats and encryption motives
In terms of why organizations place so much emphasis on encryption the results of the survey were a little surprising. Perceptions about the most significant threats to the exposure of sensitive or confidential data indicate the risk of mistaken exposure is more than twice the risk of malicious attack. Other than employee mistakes, unintended leakage triggered by e-discovery and forensic requests and general malfunctions make up the most common sources of accidental exposure. That perhaps explains why organizations site protecting their reputation and otherwise lessening the impact of data breaches – the logic being that if sensitive data is inevitably going to be lost then encryption provides a good way of mitigating the impact. Of course some organizations in certain industry sectors have no choice but to use encryption and not surprisingly compliance with mandates was ranked as the third in the list of drivers.
Key management and the ‘encryption maturity curve’
When it comes to how organizations deploy encryption there were also some surprises. More than two thirds of respondents said that their organization used five or more different encryption technologies ranging from encrypting data on laptops to databases, in applications and clouds and across networks and email systems. What emerged was a fragmented picture with no single area emerging as the dominant usage scenario.
However, an interesting trend to emerge is a clear shift of interest from relatively mature static technologies such as laptop encryption and network encryption towards more sophisticated deployments that focus on protecting data in real-time as it is used within applications, databases and cloud based services – the notion of an ‘encryption maturity curve’ seems to be emerging. The further an organization moves up the encryption maturity curve, the more important their key management strategy becomes, as complex use cases require much more contextual policies. Although the perennial boggy-man of performance still ranks as the top concern when deploying encryption it is now closely followed by concerns over key management and enforcement of policy. That’s probably why 38% respondents now say that they have a formal key management strategy and overall they report a 25 percent increase in spending on key management solutions as a proportion of encryption budgets.
The new Key Management Interoperability Protocol (KMIP) standard that allows organizations to deploy centralized key management systems that span multiple use cases and equipment vendors, has already established a relatively high level of awareness among IT and IT security practitioners, and is expected to make a major difference to encryption and key management strategies specifically around cloud, storage and application-centric deployments.
Encryption is taking centre stage as a strategic IT security issue, however key management remains a challenge that can rapidly escalate as the use of encryption becomes more widespread. Fragmented key management systems can drive up operational costs, provide attractive targets for attackers and increase the risk of losing vital keys and therefore the data they encrypted!
Influence of IT operations, lines of business and security
Edited by Stefania Viscusi
