|
In the past, Service Providers employed circuit-switched networks to guarantee bandwidth, provide resiliency, and isolate their enterprise customers� networks. However, the significant cost advantages of packet-switched networks, coupled with the ability to provide higher bandwidth services, led to a growing number of Ethernet-based Virtual Private Network (VPN) deployments.
With the recent convergence of voice and data traffic in the LAN, connecting enterprise networks has become much more complicated, given the variety of applications running with different real-time data needs. Additionally, business subscribers often want to connect multiple remote sites and have traffic pass between them with the same priority as if they were physically colocated.
The challenge with implementing this much functionality on a packet- switched network is that it is not enough to simply supply a wide pipe. A new Multidimensional Ethernet is required for operators to provide robust, reliable service across increasingly large geographies while maintaining the correct prioritization of the real time, latency sensitive traffic.
The Virtual Private Network Foundation
The foundation for meeting the demanding needs of business subscribers is the Virtual Private Network. VPNs have revolutionized Metro networks by separating physical network infrastructure from the logical deployment desired by network administrators. In this way, networks that are geographically dispersed can be treated as a single corporate LAN. VPNs accomplish this by mapping logical groupings of separate networks through tunnels that can securely traverse intermediate networks.
Additionally, the VPN structure can be expanded to provide security within a LAN based on class, type, or function of traffic. For example, Quality of Service (QoS) for voice traffic can be maintained in the presence of data traffic by grouping voice traffic separately from data traffic. Control and user data can be separated as well, giving control data first priority through the network. Traffic can even be distinguished based on function (i.e., sales, finance, engineering) to restrict access to data to only those individuals with authorization. With the introduction of new hierarchical Quality of Service capabilities, Service Providers are now able to support the unique QoS requirements of each of their diverse business subscribers.
VPN technology has evolved through several stages to serve the needs of business networks. First, isolated groups of traffic were made possible by the IEEE (News - Alert) 802.1Q VLAN standard which enabled devices to communicate as if they were on the same physical LAN, even when they were not. 802.1Q, however, has a scalability limit of 4,096 VLANs (based on a 12-bit ID field) which is quickly exhausted in Metro applications.
The IEEE 802.1ad Provider Bridges standard (also known as Q-in-Q) builds on 802.1Q by tunneling of VLANs through an Ethernet infrastructure by applying a service provider 802.1Q VLAN tag. Because these tunnels are completely isolated from other tunnels, they keep traffic separate, providing a mechanism for treating customer traffic with different priorities and QoS as it passes through the Service Provider network.
While the Provider Bridges standard improves scalability and functionality, it still fails to adequately address the needs of large Carrier Ethernet networks. The VLAN ID field limitations of VLANs still apply, limiting deployments to 4,096 Provider Bridges. Additionally, because the VPN is implemented as a large Layer 2 domain, the increasing size of the network can cause scalability challenges, as the number of MAC addresses that must be learned requires equipment with larger forwarding tables, which are typically expensive to implement.
Attempts to overcome these limitations using MPLS Layer 3 VPNs have likewise fallen short. When implemented at Layer 3, MPLS requires that private routes associated with each customer are shared with the provider, requiring customers to partially give up control and security of their networks. Additionally, these shared routes must be stored in a Virtual Route Forwarding (VRF) table and a separate VRF table kept for every active VPN, placing a tremendous strain on core router resources.
MAC-in-MAC Technology
The proposed IEEE 802.1ah Provider Backbone Bridges standard, also known as MAC-in-MAC, provides an important piece necessary to cost-effectively scale Ethernet networks. Coupled with recent developments in hierarchical QoS, the MAC-in-MAC standard brings the necessary scalability, granularity, and resiliency to enable next generation Carrier Ethernet networks.
The name MAC-in-MAC comes from the way a customer�s Ethernet frame is encapsulated with a Service Provider MAC header as it enters the Provider 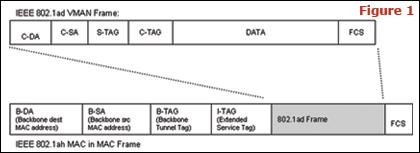 Backbone Bridge (see Figure 1). The Ethernet packet is then switched across the Service Provider network and the MAC-in-MAC header removed on the egress switch. In a MAC-in-MAC network, the customer is no longer tied to a 12-bit VLAN ID. MAC-in-MAC provides millions of service instances, removing scalability as an implementation barrier. Backbone Bridge (see Figure 1). The Ethernet packet is then switched across the Service Provider network and the MAC-in-MAC header removed on the egress switch. In a MAC-in-MAC network, the customer is no longer tied to a 12-bit VLAN ID. MAC-in-MAC provides millions of service instances, removing scalability as an implementation barrier.
MAC-in-MAC also supports hybrid networks which employ Q-in-Q VPN technology. An example of this is a network operator connecting several Q-in-Q based metro networks with a large regional or national MAC-in-MAC Provider Backbone. This eases the migration to larger networks while placing less strain on carrier resources and reducing the complexity and cost of the new infrastructure. As a result, a network can utilize the various VPN technologies together to create the optimal use of network resources based on the network architecture, location, and density of enterprise customers.
Multidimensional Ethernet
Multidimensional Ethernet enables carrier networks to meet these new performance and scalability requirements while maintaining the superior economics that drove the widespread adoption of Ethernet technology. In addition to MAC-in-MAC, Multidimensional Ethernet includes Hierarchical QoS and a SONET/SDH-like resiliency to provide the necessary complementary technology.
Hierarchical QoS utilizes hardware-based controllers to manage bandwidth and priority on a per application basis while supporting multiple QoS levels for thousands of business subscribers without impacting the performance of the network. Providing optimum Quality of Service for business subscribers requires a different approach from the models often seen in residential network deployments. It is fairly straightforward to assign a bandwidth profile to residential subscribers that may choose from some small number of subscription offerings. Business subscribers, on the other hand, typically negotiate contracts on an individual basis, and have much more dynamic requirements around QOS for their varying applications. During the Webcast of a company training video, for example, voice over IP traffic that normally has plenty of bandwidth could be interrupted if priorities are not mapped correctly.
With the advent of Multidimensional Ethernet, new algorithms now exist to handle the different requirements of business subscribers. These new priority-based algorithms allow the subscriber IT manager to set the priority of the various enterprise applications and the service provider can simply honor those settings within a fixed bandwidth profile across the VPN. The user no longer needs to decide the exact bandwidth requirements of each application. Within the bounds of the overall bandwidth profile, the service provider simply delivers the highest priority traffic first. When the highest priority applications are idle, the lower priority applications 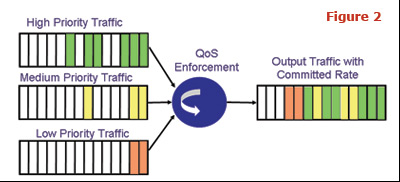 are allowed to send their data (see Figure 2). This greatly simplifies the planning process for the subscriber, and also makes it easier for the network operator to market and sell business VPN services. are allowed to send their data (see Figure 2). This greatly simplifies the planning process for the subscriber, and also makes it easier for the network operator to market and sell business VPN services.
Scalability and Quality of Service, however, must be matched with five nines carrier-class reliability if Carrier Ethernet is to succeed. Additionally, failure avoidance and recovery mechanisms must extend beyond merely restoring broken connections to address the applications and services supported by the network in order to guarantee that services are not interrupted in the event of equipment failure.
Ethernet Automatic Protection Switching (EAPS) � also known as IETF RFC 3619 � is a widely installed service-aware protection protocol that utilizes a standard Ethernet MAC and a ring topology to provide carrier-class failover response within 50 ms (see Figure 3). EAPS enables service providers to select primary/backup designations on a per VLAN basis, promoting route diversity and provisioning of service flows across multiple switches and rings. When working in conjunction with technologies such as IEEE 802.1ag 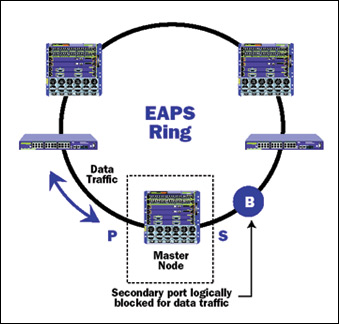 CFM (Connectivity Fault Management), protection mechanisms such as EAPS harden Multidimensional Ethernet networks, providing high reliability and availability. CFM (Connectivity Fault Management), protection mechanisms such as EAPS harden Multidimensional Ethernet networks, providing high reliability and availability.
MAC-in-MAC and Hierarchical QoS are critical enabling technologies behind Multidimensional Ethernet for bringing scalability and real-time services to the Carrier Ethernet network. By overcoming the privacy, scalability, and performance limitations of earlier VPN implementations, Multidimensional Ethernet simplifies network architecture and reduces deployment costs while enabling Network operators to deliver robust business networks with unsurpassed Quality of Service. IT
Peter Lunk is director of service provider marketing at Extreme Networks (News - Alert). For more information, please visit the company online at www.extremenetworks.com.
If you are interested in purchasing reprints of this article (in either print or PDF format), please visit Reprint Management Services online at www.reprintbuyer.com or contact a representative via e-mail at [email protected] or by phone at 800-290-5460.
|

