To take advantage of mobility and cost savings, enterprises are deploying dual-mode phones, which automatically switch between WiFi and cellular networks. By leveraging internal IP PBXs to handle calls using VoIP, rather than using the cellular network alone, enterprises can decrease costs, especially roaming charges, and provide improved mobility. Yet, many enterprises have yet to fully review the potential security implications of using dual-mode phones over public or home-based WiFi networks.
To effectively deploy WiFi/dual-mode phones securely, enterprises must address firewall issues when the user is outside the enterprise network. Besides encrypting the signaling and media traffic for privacy, and authenticating the phone and user, enterprises need to provide measures to not only simplify firewall rules but also block rogue devices and unauthorized users attempting to register.
In addition to enforcing unified communication policies that control who can talk to whom using which device, network and application, enterprises must also monitor for signatures and anomalies. These can arise from legitimate endpoints that might have been compromised or spoofed by Internet-based VoIP scripts and bots that can exploit vulnerabilities in the VoIP infrastructure and devices.
In fact, over the past four years, the Sipera VIPER Lab has identified thousands of device specific and general VoIP vulnerabilities, most of which are not addressed by traditional data security measures. These vulnerabilities can allow remote attackers to carry out spoofing and denial-of-service attacks, unwanted reboots, uninitiated toll calls, and, as recently demonstrated at Black Hat 2007 by Sipera, allow hackers to take over the device and either steal or delete data.
This article will examine some WiFi/dual-mode phone vulnerabilities and explore how these might be exploited by hackers. Once identified, we can explore security best practices and the requirements for a comprehensive VoIP security solution.
WiFi/Dual-Mode Phone Architecture
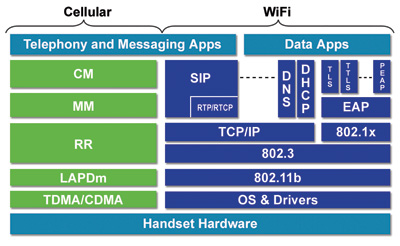
Dual-mode phones generally use either an IEEE 802.11 (WiFi) signal or cellular radio, such as GSM or CDMA, to transmit and receive voice and data. WiFi only phones, on the other hand, use WiFi signals only. Both types of phones can automatically detect a WiFi signal and connect to the access point, using a configured security profile. Figure 1 (on opposite page) shows a sample protocol stack in a dual-mode phone.
When connected to a WiFi access point, such phones are assigned an IP address, typically using DHCP. In addition to the standard TCP/IP stack, these phones have implemented one of the call setup protocols such as Session Initiation Protocol (SIP), Unlicensed Mobile Access (UMA), H.323, or Cisco Skinny Call Control Protocol (SCCP).
It is now obvious that the traditionally closed cell phone using the operator is wide open to Internet-based software and connectivity. While this offers tremendous value and ubiquitous connectivity, it also makes the phone prone to attacks similar to other Internet-based devices. More importantly, unlike other Internet applications, the phone acts like a server in that it is always ready to receive calls, enabling anyone to send unsolicited messages to the phone and either activate the ring tone or initiate denial of service attacks.
Attack Vectors
Unlike servers, though, WiFi/dual-mode phones have limited processing resources. Many enterprises that have adopted WiFi/dual-mode phones deploy thousands of these devices with various software loads. Unlike laptop and desktop PCs, which are standardized, enterprises generally find it difficult to control the software images on these devices, which creates more opportunities for rogue devices to exist on the network.
Consequently, while connected to the WiFi access point, phones can be exposed to the following threats:
1. Reconnaissance: Unlike email and web only enabled devices, SIP-enabled phones act as a server and open well known UDP/TCP ports (5060 for SIP) to receive calls, making it easy to discover them as active endpoints on the subnet. Simple tools, such as SIPScan (www.voipsa.org/Resources/tools.php ) can be used to perform this scanning and discovery operation. Subsequently, such a discovery may help in sending specially crafted packets directly to the phone.
2. Wiretapping: VoIP calls made over WiFi connection may be tapped if the wireless connection is not secured enough, or if the phones do not support strong encryption and authentication algorithms.
3. Spoofing: Phones using UDP and, in some cases, TCP, as their default/primary SIP transport, and not properly authenticating callers, are exposed to Caller ID spoofing. In many instances, when the user is in a different domain, Caller ID cannot be tied to authentication credentials. It is easy to hide behind a SIP server and spoof the Caller ID for many users. This can result in well known phishing and identity theft scams. More importantly, some voice mail systems blindly depend on Caller ID based access, making them an easy target for voice mail theft.
4. Replay attacks: SIP servers using digest-based authentication are vulnerable to replay attacks where the SIP message, with user credentials, are replayed but use a different user identity. It is possible to alter or delete user records from the server, causing denial of service to the legitimate user.
5. Supplementary services: SIP phones use DHCP and DNS services, followed by TFTP/HTTP for configuration and firmware download. These services can be manipulated to cause attacks on the phone and the infrastructure.
6. WiFi to Cellular hand-off: Availability of both WiFi and cellular protocol stacks in a dual-mode phone exposes the cellular network to threats from WiFi. A buffer overflow vulnerability in a WiFi/dual-mode phone can be exploited to execute arbitrary code, allowing the phone to be used as an entry point into a cellular network.
At the same time as phones are exposed to the generic protocol threats above, implementation flaws can creep into released versions of products as a result of programming mistakes that are not identified beforehand. The probability of these flaws being present in the released software increases with the complexity of the software. With that in mind, it is important to note that the SIP protocol specification, unlike binary protocols, is very flexible, making it extremely challenging, if not impossible, to write robust SIP message parsing implementations.
For example:
- SIP protocol messages are ASCII based, containing several headers and subheaders separated by several delimiters.
- Lengths of headers and fields inside the headers are not fixed and are only parsed using delimiters.
- SIP also supports optional headers and proprietary extension headers.
- There are several standards specifications used by VoIP applications, apart from SIP specification, which adds to the complexity of implementation. (Most of them can be found at http://www.iana.org/assignments/sip-parameters.)
Specific Threat Advisories for WiFi/Dual-Mode Phones
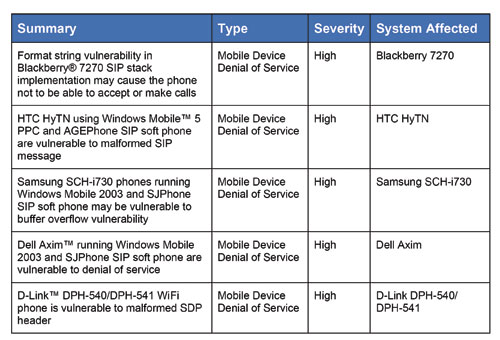
When combined, the attack vectors and implementation flaws can be used to launch exploits against WiFi/dual-mode phones. Table 1, from Sipera VIPER Lab, is but a sample of specific Denial of Service vulnerabilities that have been identified for WiFi/dual-mode phones.
Comprehensive VoIP Security for WiFi/Dual-Mode Phones
So far, we have discussed some vulnerabilities already discovered in WiFi/dual-mode phones, described the challenges in building robust SIP implementations, and shared some specific exploit examples. But, to truly secure enterprise VoIP networks, enterprises must also adopt and enforce security best practices for VoIP and WiFi/dual-mode phone users, including:
- Keeping security patches up to date.
- Enforcing strong authentication and encryption wherever possible.
- Securing WiFi access points.
- Using VLANs to keep voice and data traffic separate and police the bridges between the two VLANs.
- Appling VoIP intrusion prevention techniques
Sitting at the edge of the enterprise network, usually within the DMZ, a dedicated, comprehensive VoIP security box can address many of the issues raised above and ensure best practices are followed. Such a purpose-build appliance must solve firewall/NAT traversal, terminate encrypted traffic to the enterprise when the WiFi/dual-mode phone is external to the enterprise, and offer fine-grained policy enforcement to apply different security and call routing rules for the same dual-mode phone, depending on whether it is inside the enterprise or outside the enterprise. But, most importantly, any dedicated VoIP security solution should protect against signaling and media vulnerabilities through sophisticated VoIP-specific security methodologies.
When evaluating a VoIP security device, enterprise should look for those that are aware of the complex nature of VoIP protocols, and can conduct detection, mitigation and prevention in real time. Further, such a device should also be able to understand user behavior, as this is the most effective method of analyzing and eliminating false positives/ negatives, which can be extremely damaging to the VoIP service and user experience. Together, these practices proactively protect the VoIP service from attacks, misuse and service abuse which networks and end-users face today and in the future.
Krishna Kurapati is the Founder and CTO of Sipera Systems, a leader in pure security for VoIP, mobile and multimedia communications. For more information, Sipera can be reached at 214-206-3210 or www.sipera.com.
Richard "Zippy" Grigonis is Executive Editor of TMC's IP Communications Group.
Unified Communications Communications Magazine Table of Contents




