The same logic applies to sharing presence information among organizations and Ds.
Presence is often called the dial tone for the Internet age. Unlike the dial tone on your phone, presence tells you not whether you are connected to the network but whether your contacts are connected. This means that presence lets you know ahead of time whether your contacts are available for communication, what their capabilities are, and so on. But it also means that the true value of presence emerges only when the people and services you want to communicate with are part of the network in the first place.
In the presence vernacular, a service is �federated� when it is connected to the broader network. Whereas traditional telephony networks relied on complicated peering relationships to establish federation, on IP-based networks federation can be more straightforward. For example, no one even thinks about federated communication among email systems. Instead, it just happens, which means you can send email to anyone, anywhere, no matter what email service they use.
As we�ve discovered since commercial email services first arose in the early 1990s, the email model of dynamic but unverified, insecure, untrusted federation has its downside. One of the most obvious symptoms of the email federation model is the proliferation of spam, which has reduced the value of email. So those who deploy presencebased systems such as IM and Voice over IP (VoIP) are eager to develop a smarter approach to federation.
Thankfully, the designers of Internet-standard presence technologies such as Session Initiation Protocol (SIP) for Instant Messaging and Presence Leveraging Extensions (SIMPLE) and Extensible Messaging and Presence Protocol (XMPP) incorporated lessons learned from the email experience. In particular, we can recognize several different grades of federation using IP-based presence technologies (See Table 1).
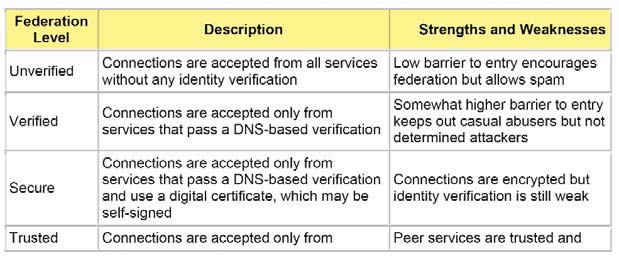
Table 1
Even trusted federation is not necessarily the end of the story. What kind of certificates will you trust? Will you trust �Class 1� certificates, which require only basic verification that the service administrators are associated with the domain (e.g., via a whois lookup)? Will you trust only �Class 2� certificates, which require more in-depth identity verification procedures? Which certification authorities (CAs) will you trust? Will you work with other organizations in your industry or supply chain to set up a special-purpose CA (News - Alert)?
In the XMPP community, we have been working on some of these issues over the last year or so, although we can�t yet claim to have all the answers. For example, in December 2006 we launched a dedicated intermediate certification authority for XMPP-based presence services, which has issued over 500 Class 1 certificates so far. We have also begun to define best practices related to the deployment challenges involved in trusted federation, and will be refining those recommendations over the next few months.
It may seem as if working towards trusted federation isn�t worth the trouble. While many organizations may decide that�s true, others will see the benefits of sharing presence across trust boundaries. As we move from the old telephony world to the brave new world of IP-based unified communications, we will need to accept that our federation models need to be brought up to date as well. And because it is a powerful catalyst for communication, presence may be the first technology that requires attention.
Just as telephonic communications have crossed trust boundaries for decades (mostly a success) and email communications have done so for the last fifteen years (the jury is still out), the presence-enabled, IP-based unified communications technologies of tomorrow will need to cross trust boundaries in order to achieve maximum personal benefit and organizational productivity. Innovative enterprises and Ds are beginning to see that the power of presence can be fully realized only when it is shared. In a federated world, you�ve got to give some to get some.
Peter Saint-Andre is director of standards at Jabber, Inc. Large enterprises and Ds have understood the value of the Jabber, Inc. commercial platform, known as the Jabber Extensible Communications Platform� (Jabber XCP�), and today there are hundreds of organizations using it as an enterprise instant messaging (EIM) solution and extending it into other real-time, presence-enabled applications and services. For more information, please visit the company online at www.jabber.com.
Unified Communications Communications Magazine Table of Contents





