|
With the increasing ability of smartphones and data-enabled cell phones to store sensitive data and documents, conduct financial transactions, and access corporate networks, both consumers and corporations should be increasingly concerned with the security of their mobile devices. Identity, authentication, and platform integrity have become critical capabilities for mobile devices. Today’s cell phones implement these capabilities at vendors’ discretion, without a clear industry-wide consensus on the fundamental requirements and best practices. However, a recently announced open-industry specification by the Trusted Computing Group (TCG), an industry organization providing specifications across a variety of platforms and devices, promises to change the security environment on mobile devices for protection of personal information, ticketing, mobile commerce, content protection, and more.
Mobile Security Threats and Opportunities
Perhaps the biggest security threat that mobile users face today is the loss or theft of their phone. As well as its obvious value as a physical device, the phone may contain personal and financial data: stored in the handset or in the removable Subscriber Identity Module (SIM card). While a stolen SIM can be barred by a mobile network once the theft has been reported, it is much harder to effectively bar the handset from being used with a different SIM. Also, unless the user has protected his personal and financial data by a PIN (and many users do not), these data could be accessed by an unauthorized party. Emerging threats to mobile devices arise from these products becoming increasingly more open and more sophisticated, using additional sensitive information stored on the phone itself (e.g. personal photos, emails, contacts, and calendar items). In addition, mobile products are increasingly similar to PCs, or interface to PCs, or communicate with computer networks. This provides the potential for the types of attack that are currently restricted to PCs, so phones will need defenses against those attacks.
With more and more handheld devices capable of receiving email, security, especially in corporate email with sensitive internal and external data, is a major concern. Receiving or sending email requires connectivity to a network. This means that a mobile device can access data that previously would have been only available by a PC. More and more devices have this capability today and it certainly will become an expected feature on a variety of high-end mobile products. Certainly, smartphones will include this capability.
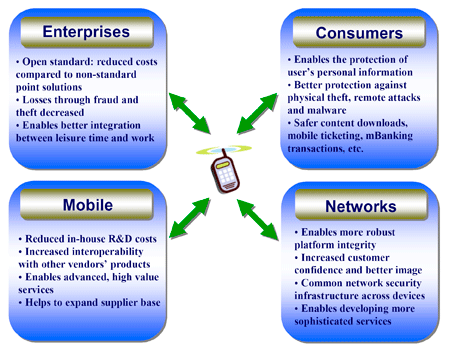 |
Figure 1. The Mobile Trusted Module supports multiple stakeholders and addresses specific concerns. |
|
|
Without standards, any security implementation winds up being a proprietary, point solution. Here is where the pitfalls and opportunities lie. Security should be implemented in a way that allows users to interact with computers and avoids creating artificial barriers. If mobile phone security is implemented in an inappropriate manner, it is almost guaranteed to become a barrier to interoperability between future generation mobile phones and future generation PCs and servers. In any case, a standard can usually be upgraded more easily and meaningfully than a proprietary solution.
These are just a few of the reasons that justify the need for a specification for greater security and better service and applications. The acceptance and success of any effort to prevent threats and improve security must be a standards-based approach.
TCG and Trusted Mobile Devices
The Trusted Computing Group (TCG) is an industry organization providing specifications across platforms and devices and is the focal point of security standardization for computing devices. To provide integrity, authentication and identity and have security functions which are cost-effective, transparent to users, reasonably implemented, and interoperable, the organization released use cases, or anticipated applications for mobile security, as a first step to an open-industry specification (MINI URL #1 TO COME). In September 2006, TCG announced the industry’s first open-standard specification to enable mobile security to be embedded in a device’s basic architecture and interoperable with the existing trusted computing framework, the TCG Mobile Trusted Module (MTM) Specification (MINI URL #2 TO COME).
While TCG’s effort is new for mobile phones, it is well-established for computers. TCG approved its Trusted Platform Module (TPM) specification in 2000 and since that time, some 50 million PCs have shipped with integrated circuits that conform to this specification. In 2007, the TPM took a giant step forward with Microsoft Vista, which uses functions provided only by a TPM. The BitLocker™ (MINI URL #3 TO COME) in high-end versions of Vista, targets enhanced data protection from computer thieves and hackers. Using TPMv1.2, it protects user data to ensure that the PC was not tampered with when the system was offline. Vista will most likely make the use of the TPM much broader and a lot more commonplace. Note, however, that just as the TPM in a PC was used before Microsoft’s Vista, the MTM in a mobile phone can be used without Microsoft software.
Even the Federal Deposit Insurance Corporation (FDIC) Division of Supervision and Consumer Protection Technology Supervision Branch, in its report “Putting an End to Account-Hijacking Identity Theft — Study Supplement” (MINI URL #4 TO COME), recommended multifactor authentication including a TPM to protect identity and data.
The Mobile Trusted Module is as similar to the TPM as possible but the Mobile Reference Architecture (MINI URL #5 TO COME) comprehends the regulations and restrictions that affect cellular products. For example, the development of a Mobile Trusted Module and the Mobile Reference Architecture took into account the interest of various stakeholders that include the user/owner, the device manufacturer, the network service provider and others such as enterprises and third parties. Figure 1 shows these key stakeholders and the different issues solved by the MTM.
Establishing Trust
Building trust in a piece of hardware, software or network is not unlike the process that an individual uses to establish trust in a bank or garage mechanic. In this case, the trust builds on a trusted platform or trusted module. As shown in figure 2, common mobile phone building blocks are each able to show that they are trustworthy. Device, cellular, applications and user service engines all have Trusted Services. In each section, the solid rectangle represents an interface and the solid arrows between blocks indicate a dependency. The arrows point away from the dependent element. The MRTM is a Mobile Remote-Owner Trusted Module and the MLTM is a Mobile Local-Owner Trusted Module. The term Mobile Trusted Module (MTM) is a generic term for both MRTMs and MLTMs.
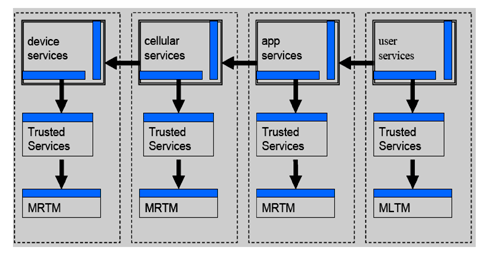 |
Figure 2. The interrelation of trusted services in a trusted mobile device. |
|
|
Secure Mobile Device Applications
As part of developing the MTM specification, 11 use case scenarios were considered that included mobile ticketing, mobile payment, and SIMLock/Device Personalization.
Using a mobile device to download and present tickets adds significant convenience when used properly but can be a serious threat because of illegal duplication, modification, or deletion. The ability to avoid problems with mobile ticketing starts with the mobile device having the built-in capability to provide secure service for downloaded applications. The ticketing application is one that could be downloaded and the platform would verify and authenticate the integrity of the application. Purchased or redeemed tickets have data objects that represent the rights and these rights are securely downloaded to the device. To use the ticket a data reader verifies the permission granted by the ticket and then treats the ticket as consumed. Once consumed, the security data linked to the application or to the ticket are deleted ending the process.
A similar process occurs for mobile commerce. Recent announcements by Citibank and AT&T address greater implementation of mobile commerce (MINI URL #6 TO COME). Mobile commerce is among the potential applications that were considered in the establishment of the MTM spec. The trend towards higher value services means that security will be an absolute requirement. Other financial services outside the voice realm provide an enabler to move forward and perform tasks/functions that have not been possible in earlier generations of phones and hardware.
Another interesting application is the corporate network access control. With remote access capability and broadband wireless capability in a PC, and the same capabilities in a portable communication device, corporate networks could use a TPM (in a PC) or MTM (in a mobile phone) as part of their network access control strategy. The Trusted Network Connect Work Group of TCG addresses these aspects across multiple platforms, peripherals, and devices (MINI URL #7 TO COME).
A Trusted Infrastructure
Service providers and carriers certainly would benefit from a more trusted infrastructure, but TCG’s mobile group deliberately avoided reinventing the wheel. Part of the objectives of the TCG’s mobile group was to avoid unnecessary redefinition of cellular network infrastructure and to avoid creating a different infrastructure to that expected to be deployed for trusted access to PCs. The result is minimal change to existing cellular networks and use of the same specifications as trusted PCs whenever possible. This means that companies can use similar backend infrastructure for both PCs and mobile devices.
One point worth noting is that the SIM is unlikely to disappear and will continue to provide the flexibility of having a removable element that carries the user’s identity from device to device. The MTM is designed for platform security and the SIM is primarily for user security. They perform quite different functions. The MTM can be used to provide device protection to deter device theft and use of a subsidized product on another service provider’s network, which does not replace the SIM, for example.
Confidence Via Public Specifications
With technology that uses full-strength encryption algorithms, and specifications open to inspection, the TCG specifications have been analyzed to identify potential shortcomings and flaws, and improved and enhanced by numerous knowledgeable experts. Through the participation of the key companies involved in the development of the specification, a considerable amount of time and effort has been expended to ensure the trustworthy aspect of the MTM specification. The thoroughness builds on the TCG’s TPM and efforts that started over seven years ago to create a trusted environment for mobile products.
Janne Uusilehto is the Head of the Product Security Technologies Team, Nokia (www.nokia.com). For more information visit the Trusted Computing Group at www.trustedcomputinggroup.org.
|

