Security Feature
Password Verification and Authentication: How to Combat Cyber Crime
As the level of technology increases and things get better in the field for all users, the importance of ensuring all data is protected is heightened. Cyber security is something that many experts are becoming increasingly more concerned with as each year passes. Many companies are looking for ways to make information more secure and protected. One of those ways that has become very prominent is two-step verification and authentication for applications as well as the web.
Increased Cyber Crime
Security breaches increase in number with each passing year. While the breaches that are known about are disclosed, there are some that are never even detected by companies. The early January theft of more than 320,000 user emails and passwords from cable giant Time Warner (News ![]() - Alert) gave validation to the argument that simple password authentication is becoming less and less reliable.
- Alert) gave validation to the argument that simple password authentication is becoming less and less reliable.
A recent PwC survey that 79% of the executives had detected an incident regarding security over the past year. There seems to be endless ways in which one must avoid password pitfalls – weak passwords, shared passwords, unchanged passwords and default passwords. Even following all of the best practice guidelines, some things remain out of your control including how committed your provider is to encrypt and protect your credentials on its server.
Two Step Verification and Authentication
More and more companies, websites and application platforms are requiring a second factor authentication process to allow users to log into their account. There are three types of authentication: something you know” (knowledge factors), “something you have” (possession factors) and “something you are” (inherence factors). After entering your password, you receive a numeric passcode, via SMS text messaging, that you’re required to enter in order to gain access. Seems familiar…like another password, right?
Two-step (or multi-step) verification is simply an extension of single-factor authentication by requiring that the user submit several distinct verification occurrences that fall within the same type of the three authentication factors. The question then becomes – how does a two-step, single-factor verification process increase the security of data when in recent malware attacks, we’ve seen the interception of two-step verification tokens as it is transmitted to the user?
Amazon Has a Snappy Idea
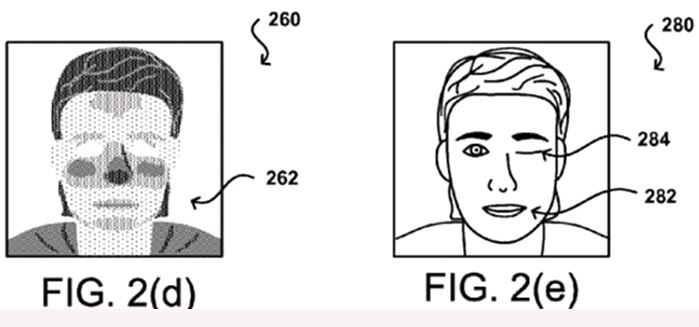
The power of the selfie knows no bounds! A patent application was recently filed by the online retailer for a two-step photo verification process for logging in to website to buy products online. When you’re ready to make a purchase, the Amazon app would ask you to frame your face on the screen using the front-facing camera. The company would then use special facial recognition technology to make sure it’s you and confirm the purchase. The process identifies the user image information corresponds to a living human using one or more human-verification processes. Selfie verification would not only be more convenient for the user, but also more secure. It wouldn’t force users to look for shortcuts to remembering passwords, which in turn makes them more vulnerable to hackers as the demand and need for information security increases.
About the Author

Laura McGarrity joined Mondo in 2012 and currently serves as VP of Digital Marketing Strategy, She guides Mondo’s (a tech and digital marketing recruiting firm) brand strategy through inbound marketing, including blogging, public relations, field marketing programs, search engine optimization, video marketing, and social media as well as heading up MondoLabs, Mondo's in-house full service digital marketing agency.
Edited by Peter Bernstein