Security Feature
Gemalto 2015 Breach Level Index Findings Provide Granularity on Global Activities
The massive 2016 RSA Conference in San Francisco starts February 29, and it already is shaping up as quite the show. Indeed, this year’s show is a kind of perfect storm. It comes at a time of a slew of reports about why last year was a good one for the bad guys, a myriad of innovative new products and services to protect data on the move and at rest, and of course at a time when data breaches are making headlines and the Apple v. FBI imbroglio remains unresolved.
With that as context, I have been pointing out, on various TMC (News - Alert) sites, the latest reports you can use to get a firm background on all things relating to cybersecurity.
One of the reports that I highly recommend for IT security professions is digital security solutions provider Gemalto’s (News - Alert) Breach Level Index. The reason, I am sorry is say, is (as shown below) that its major headline is that in 2015 there were 1,673 data breaches that led to 707 million data records being compromised worldwide. And, the breakdown associated with the type of breach is not exactly encouraging either.
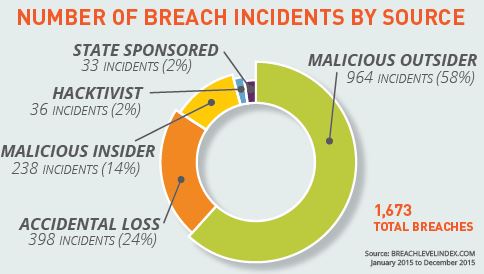
This report is significant as the Gemalto Breach Level Index (BLI) is a global database that tracks data breaches and measures their severity based on multiple dimensions. These include:
- The type of data and the number of records compromised
- The source of the breach
- Whether or not the data was encrypted.
It assigns a severity score to each breach, provides a comparative list of breaches, and “distinguishes nuisances from truly impactful mega breaches.”
Commenting on the findings, Jason Hart, Vice President and Chief Technology Officer for Data Protection at Gemalto noted:
“In 2014, consumers may have been concerned about having their credit card numbers stolen, but there are built-in protections to limit the financial risks… However, in 2015 criminals shifted to attacks on personal information and identity theft, which are much harder to remediate once they are stolen. As companies and devices collect ever-increasing amounts of customer information and as consumers' online digital activities become more diverse and prolific, more data about what they do, who they are and what they like is at risk to be stolen from the companies that store their data. If consumers' entire personal data and identities are being co-opted again and again by cyber thieves, trust will increasingly become the centerpiece in the calculus of which companies they do business with."
One of the several alarming trends which are in the report is that state-sponsored attacks accounted for 2 percent of data breach incidents, but the number of records compromised as a result of those attacks totaled 15 percent of all records exposed. It underscores why the Obama administration in the U.S. recently outlined its intention to beef up cybersecurity protection of sensitive government data, and share more information with the private sector.
Not all data breaches are created equal
Hart also explained a very salient point that not all data breaches are the same which is why the severity is important when assessing what needs to be protected. He added what almost every vendor in the space has said: “Unfortunately, this year there were several major breaches involving personal data and identities that were not encrypted when they should have been."
The entire issue about what is, can be and should be encrypted and who should hold and manage the keys is at the center of the Apple v. FBI case. However, this really is way more than just about what happens with a single iPhone (News - Alert) as we know from everyone who has weighed in on both sides of the issue. This is about trust. And, as the debate heats up, who and how much all of us can and should trust is going to shape how we and individuals and enterprises going forward select vendors and implement various security solutions.
Exercises such as the various breach indices like that from Gemalto are important tools. As Hart concluded: “They provide CIOs and CSOs with the data they need to better classify breaches, conduct internal risk assessment and planning, and most importantly employ the right security technologies to help ensure that if a breach were to occur their high value and most sensitive data would not be compromised."
In short, RSA (News - Alert) and these reports amplify the obvious message, “Let’s be careful out there!”
Edited by Maurice Nagle













