Docker has taken the networking world by storm, having played a starring role in the popularization of containers.
The company’s CEO provided an update this summer on the strong uptake of Docker technology by the developer community and others. And the company at its annual customer gathering in Seattle aimed to address some of Docker’s perceived gaps in the areas of orchestration and security.
However, in mid July there were reports that Docker Cloud was down due to what appeared to be a DNS outage caused by a distributed denial of service attack.
The Uptake
Thirty to 70 percent of all enterprises are using Docker in some shape or form, Docker CEO Ben Golub noted in his speech at the recent DockerCon 2016 event. Sixty percent of those using Docker are using it in production, he added, and 25 percent of them already have their apps containerized.
Docker users come in all sizes and from a variety of verticals. Goldman Sachs is among the more high profile Docker converts, Golub indicated. The company expects to be running a quarter of its apps over Docker this year, with plans to ultimately have 90 percent of them on Docker.
There are 460,000 Dockerized apps, reflecting 3,000 percent growth in 2 years, and 4.1 billion image pulls. And there are more than 95,000 Docker projects on GitHub, Golub said.
More than 2,900 people have made Docker contributions. In the month leading up to DockerCon, on Engine alone, 986 people interacted with the repository, he said. Two-thirds of engine contributions are external, he noted.
Engagement by the developer community around Docker was evident at the Seattle event, where more than 4,000 attendees congregated and the exhibitor hall and general sessions were filled with an enthusiastic crowd.
Golub indicated the company is in good shape financially. He said the $180 million it raised last year hasn’t yet been used, and that company revenues are growing much faster than expenses.
Docker solutions, he added, are sold by the company’s 30-person sales force. The company also works with Accenture (News - Alert), Booz Allen, and major cloud providers, he said. Docker commercial Engine will be shipping with every HP server, he added. Docker also has a relationship with HP to sell its Docker Datacenter (through all HP sales people and the HP sales channel), he said, and Docker has a similar relationship with IBM (News - Alert).
Container Orchestration
After having seen more than 450 companies join its ecosystem, and millions of developers use Docker technology to write 460,000 apps, the company indicated it was time to take steps so these implementations can scale more efficiently across the entire enterprise. With that goal in mind, and no doubt in a move to grab a bigger piece of the valuable orchestration pie, Docker at its event announced the integration of its Swarm orchestration solution with Docker Engine.
“At the end of the day the individual container doesn’t matter. What matters is the entire system,” said Solomon Hykes, Docker founder and CTO, in his DockerCon keynote speech.
But managing an entire system requires orchestration. And, to date, organizations needing orchestration have two options, according to Hykes: They can either hire an army of experts or hand things over to a single vendor, which can result in vendor lock in. But customers wanted another option, he said, so Docker has made orchestration usable by non experts by embedding orchestration into Docker 1.12.
This integration will make things easier from an operational standpoint for businesses implementing Docker, explained David Messina (News - Alert), the company’s senior vice president of marketing. Container orchestration, he added, involves an automated set of capabilities that define distributed applications and manage them at operational scale, which is akin to a hypervisor in VMware parlance. So Docker is following the same trend line system administrators are used to – leveraging an integrated solution for more simplicity and uniformity so it’s easier to ensure apps are running as intended.
Going forward, Swarm will be available as an optional feature set of the Docker Engine, for which users can still elect to employ the orchestration solution of their choice.
“Swarm mode is something you have to turn on,” said Messina. “It’s a command.”
Docker has been in the marketplace with its Swarm orchestration solution for a while now. But it’s Kubernetes, which was created by Google (News - Alert), that is considered the leader in container orchestration. Mesos is generally considered the third big player in container orchestration. But there are plenty of players in container orchestration. So by integrating Swarm in with Docker Engine the company has moved to strengthen its play in the important container orchestration arena.
Security Enhancements
Although Docker is the typically the first name that comes up with people talk containers, there has been widespread discussion about the company’s shortcoming in the area of security.
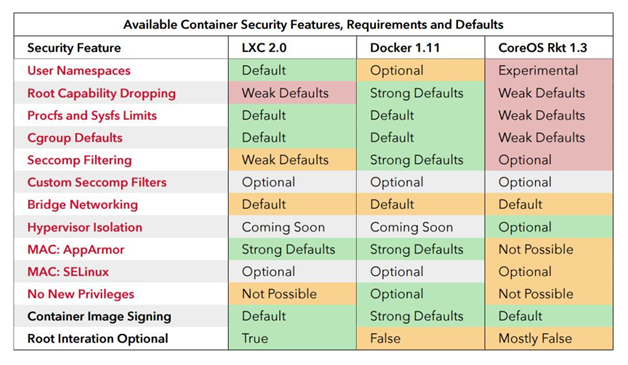
In a recent email interview with me, Docker said that the Docker platform is the most secure container runtime available today (see chart below). Current versions of Docker (1.11 and later) support AppArmor, cryptographic image signing, end-to-end cryptographic signature validation, granular control through the use of cgroups, SELinux (mandatory access control), seccomp (syscall restrictions), and user namespaces (root in the container without privileges on the host).
At DockerCon 2016 this summer, Docker introduced Cryptographic Node Identity. With it, each node (machine) in a cluster has a unique identity, allowing for workload segregation. That means that payment card workloads could be dispatched to only certain machines that have undergone a rigorous auditing process, as one use case example. Docker at the Seattle event also introduced a cluster management system that enables end-to-end encryption by default, mutual TLS authentication (to prevent against man-in-the-middle attacks), and certificate rotation (to recover from compromised credentials).
“Criticisms of Docker security typically refer to very old versions of the Docker Engine (1H 2015),” the company added. “Docker has been focused over the last year on addressing the three key areas of container security: secure access, secure content, and secure platform. The isolation and containment features are not only built into the Docker Engine but also enabled out of the box. These features allow you to have trust over the origin of your content, reduce the attack surface area of the Linux kernel, improve the containment capabilities of the Docker Engine, and ultimately help you build, ship and run safer applications.”
The Takedown
Despite these security enhancements, Docker Cloud ran into problems, and its users were down or experienced intermittent outages as a result, in mid July.
The Register on July 19 was among the media outlets that reported the news, saying the websites running on Docker Cloud were down and that the company’s customers were complaining about that and were also frustrated with Docker’s limited response to the problem.
Website Magazine on July 21 reported that “Docker notified users on its system status page that an ‘unusual’ high load on its DNS servers was causing some lookups to fail and there was a corresponding thread about the issue in its forum. That wasn't enough however for some Docker users and they weren't shy about sharing their discontent with others.”
And Avi Freedman, co-founder and CEO of Kentik, and his public relations team were approaching media outlets with commentary on the Docker outage, and provided this quote to INTERNET TELEPHONY: "DDoS is an equal opportunity disrupter of IT value chains. Today there are plenty of private and public clouds that are hosting Docker and other containers, and as distributed applications and microservices architectures grow in popularity, container deployments will grow as well. Anytime there is a dependence on internet traffic flows to deliver applications or services to internal or external users, there is potential vulnerability. “
He added that “CIOs need to develop a (digital supply-chain) game plan. This requires developing a map of all digital trading dependencies, from end users to API calls.”
Edited by Maurice Nagle




