It used to be that distributed denial of service attacks — for which the bad guys overwhelmed company servers with messages, thereby bringing web viewing and transactional capabilities to a grinding halt — were more major nuisance than possible long-term threat to enterprises.
However, as leading network security and management company Arbor Networks, in its 8th Annual Worldwide Infrastructure Security Report, recently revealed, such is not the case. In fact, what the company found was not only that the frequency of such attacks is on the rise, but the sophistication of the attackers is increasing. Equally as alarming is that DDos has become part of the growing nasty proliferation of the advanced persistent threat landscape.
For those not aware, APTs (also known as zero day polymorphic attacks because they strike with ferocity and take many pernicious and multi-vector forms) are spanning the globe and wreaking havoc for enterprises and service providers alike. These are Internet-enabled government-sponsored espionage threats. They are customized and aimed at the usual targets, but now are being used on other vectors of vulnerability to infect media, compromise supply chains, and disrupt financial institutions’ ability to conduct commerce. And, while individual hackers are not formally engaging in APT (News - Alert), since they likely do not have the resources of government-backed efforts, they have adopted many APT best (or should I say worst) practices.
It needs to be noted that confronting APT and DDoS threats was at the very top of the list of discussion among the elite of the cybersecurity industry at the recently concluded annual RSA (News - Alert) event.
Arbor finds bad actors have been busy and adaptable
The Arbor Network report is sobering as well as enlightening in terms of quantifying the landscape IT professionals are dealing with on the infrastructure side of things.
Key findings included:
· Advanced persistent threats are at the top of the concern lists for chief security officers at both enterprises and services providers.
· While the size of traditional DDoS attacks seems to have reached a plateau, there has been a marked increase in complex multi-vector attacks.
· Data centers and cloud services are increasingly victimized.
· Mobile operators increase capacity but not visibility.
The data in the report covers October of 2011 through September of 2012. One-hundred thirty respondents from a mixture of tier 1, tier 2/3, enterprise and other types of network operators from around the world were interviewed; 64 percent of respondents are network or security operations engineers, analysts or architects; the remaining are management or executives.
What was gleaned is eye opening.
APTs evolve: 61 percent named bottled or otherwise compromised hosts as their top concern, and 55 percent named APTs as the top concern. Plus, when it comes to DDoS, the largest attacked reported was 60gbps, which is roughly the same as in 2011; however, 46 percent reported multi-vector attacks. This means application-layer and multi-vector attacks are evolving and on the rise.
Data center and cloud victimization on the rise: 94 percent of data center operators reported attacks, and 90 percent of those reported operational expenses as a business impact. There’s no surprise here considering that the bad guys like bank robbers are going to where the money is.
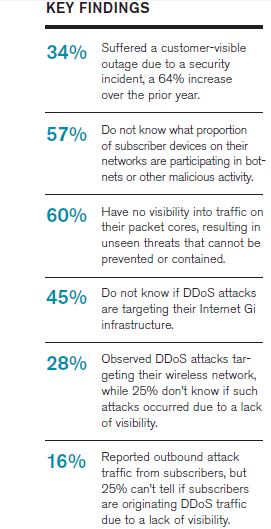
Mobile providers continue to be reactive: 60 percent do not have visibility into the traffic on their mobile/evolved packet cores. This is very troublesome; but, as Arbor noted, the economics of consumer subscriber networks do not incent providers to implement security until a problem occurs. The company also noted that, “We believe it is only a matter of time before botnets and DDoS become more prevalent within mobile infrastructure.” And, in terms of BYOD creating new challenges, 63 percent of respondents allow BYOD devices on the network, but only 40 percent have the means to monitor those devices.
The graphic below is illustrative of why mobile operators need to up their game.
Edited by Stefania Viscusi




