This article originally appeared in the July/August issue of INTERNET TELEPHONY
Wi-Fi and small cells represent new opportunities for mobile operators, but also come with new security risks that must be addressed. Given the extraordinary uptick in data consumption via 3G- and 4G-enabled devices such as smartphones and tablets, operators are investing in the next generation of small cells to enhance the benefits provided by microcells deployed in the late 1990s and early 2000s.
These new small cells allow operators to access additional spectrum, use existing spectrum more efficiently, and promote greater deployment flexibility, all at a lower cost. They also reduce radio access network build-out and backhaul investment, while improving the end user experience by providing increased access to mobile networks. In addition, because they can be held in the palm of one’s hand, they reduce a base station’s footprint and have less environmental impact in terms of power consumption and obtrusive objects in the public domain.
This next generation of small cells can be broken into four main types:
- 3G/4G femtocells for closed user groups;
- public access small cells;
- mobile operator-deployed Wi-Fi access points; and
- public Wi-Fi WLAN access points.
The specific security issues vary across each small cell type, but the solution can be found in variations of the same 3GPP security architecture, leveraging a carrier-grade, highly-scalable security gateway.
Common Security Vulnerabilities across Small Cells
When small cells, including Wi-Fi WLAN, are rolled out in volume, it will be into an increasingly IP-oriented mobile network environment where the security vulnerabilities are inevitably greater. Because most of these Wi-Fi and small cell deployments rely on an untrusted IP network, security risks increase for both control and user plane channels. For example, in cases where small cells need to leverage pre-existing fixed access networks for backhaul via a DSL connection, the mobile user’s traffic is liable to be exposed to the untrusted open Internet environment, rather than managed end-to-end across the mobile operator’s dedicated trusted facilities.
As a result, data encryption becomes increasingly important and challenging. For example, femtocell user traffic is no longer protected by 3GPP encryption, but is clear text that could potentially be intercepted. In LTE (News - Alert) the 3GPP-mandated encryption terminates in the eNodeB but there is no native or embedded encryption in LTE between the eNodeB and the core of the network. Moreover, when encryption is terminated in the 3G public-access small cell, the operator needs to encrypt it again across the backhaul to secure it effectively.
In addition, because small cells are more likely to be deployed in a relatively open and accessible public place, such as a shopping mall, street light or other utility pole, they are easier for unauthorized parties to physically tamper with and potentially compromise. A public access small cell that has a radio-based backhaul that is a physically separate unit will have the additional vulnerability of possible interception of traffic in the wired or wireless communication path between the two devices.
While there will be very little difference in the security architectures that mobile operators use for femtocells, the greater disparity and complexity associated with deploying and managing public access small cells will give rise to a lot more variation in the security model that operators adopt as these are rolled out. For example, Wi-Fi has a unique set of security challenges that must be addressed.
Trusted Wi-Fi Access
Because it operates in unlicensed spectrum that is more vulnerable to interference than licensed 3GPP spectrum, Wi-Fi has traditionally been considered something of a poor relation to licensed cellular radio standards in mobile operator circles. Mobile operators do have experience leveraging Wi-Fi, but it is typically as a parallel access network to the mobile network. However, Wi-Fi is popular with subscribers. According to the comScore (News - Alert) data referring to the U.S. market in Q3 2011, customer smartphone usage is now split evenly between Wi-Fi and 3GPP access networks. Furthermore, the number of connections on AT&T’s (News ![]() - Alert) Wi-Fi networks has increased from 20 million in 2008 to 745 million by the end of the third quarter in 2011.
- Alert) Wi-Fi networks has increased from 20 million in 2008 to 745 million by the end of the third quarter in 2011.
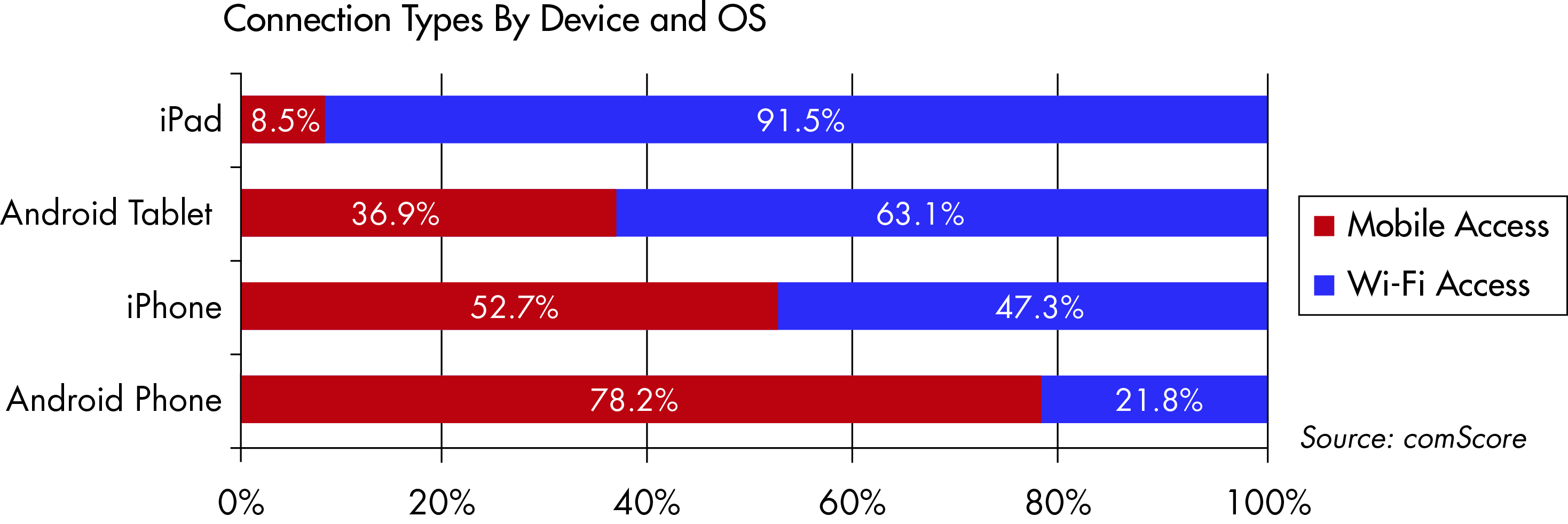
According to the comScore data referring to the U.S. market in the third quarter of 2011, customer smartphone usage is now split evenly between Wi-Fi and 3GPP access networks
As a result, mobile operators around the world are looking again at how they use Wi-Fi to handle rising data traffic volumes and complement their service offerings. With its origins as a self-deployed home and enterprise access technology, security wasn’t a key consideration in the evolution of Wi-Fi. The resulting ease with which countless numbers of users have had sensitive, personal information copied and stolen is well known, but a lot of work is being done to render Wi-Fi networking more secure in terms of both the user-facing air interface and the network-facing transport or backhaul service.
3GPP Security Architecture Has Flexible Model for All Small Cell Types
3GPP’s unique security architecture for small cells and Wi-Fi offload has proven to be highly secure, which is demonstrated through its successful support for the two million femtocells in service today. The key feature of 3GPP’s femtocell security architecture is that it leverages the IPsec tunnel within the femtocell for encryption and authentication of traffic as it exits the femtocell and is transported across the access network. That tunnel is then unencrypted by a SEG in the operator’s core network.
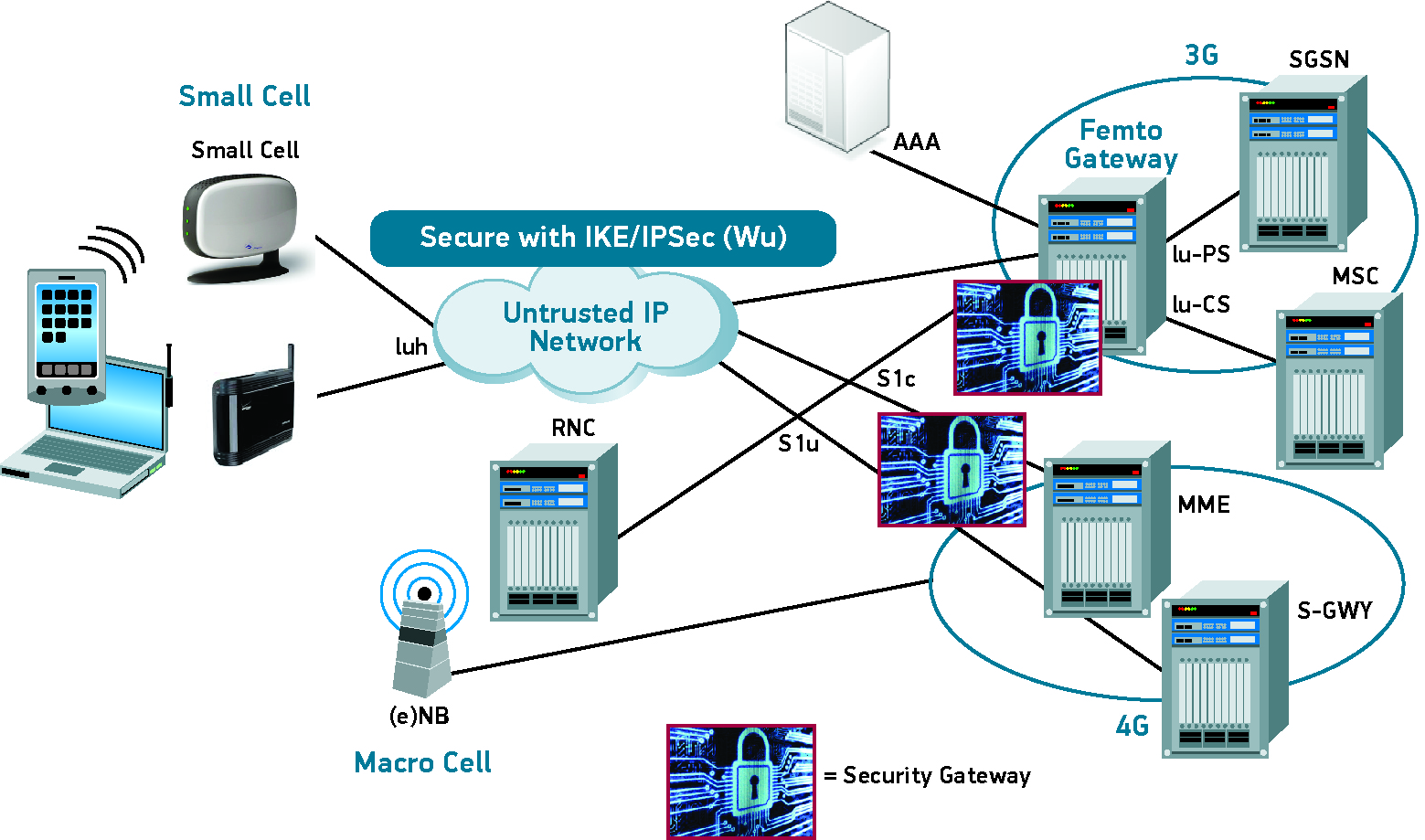
3GPP Interfaces for Small Cells
There is certainly an opportunity to reuse the same security gateway to terminate both femtocell and public-access small cell traffic. The operator can share the same security architecture across public and private domain small cells as well as the same physical equipment, providing it is able to scale sufficiently to support hundreds of thousands or even millions of subscribers. Because operators can reuse the same security infrastructure, the upfront investment is lower providing carriers with significant capex and opex savings.
SEGs and How They Function within Various Architectures
SEGs enable operators to support large numbers of concurrent, bi-directional IPsec tunnels on a stateful, high-availability system at the lowest possible cost per subscriber, while meeting the unique security challenges for each type of small cell.
For example, a North American Tier 1 operator is implementing WLAN offloading and interworking with 3G and 4G, and a mobile operator in Asia with 35 million subscribers is using Wi-Fi to offload data traffic. Both carriers are securing their networks with an LTE SEG, which serves as a common platform in the 3GPP architecture and delivers turnkey tunnel terminating gateway and interworking wireless LAN functionality, providing the operators with significant advantages in leveraging different applications of the same platform for each of the small cell types. Now network equipment providers can offer their mobile carrier customers a multitude of security services on a single blade, including LTE network domain security, firewall and an evolutionary path to supporting packet data gateway technologies.
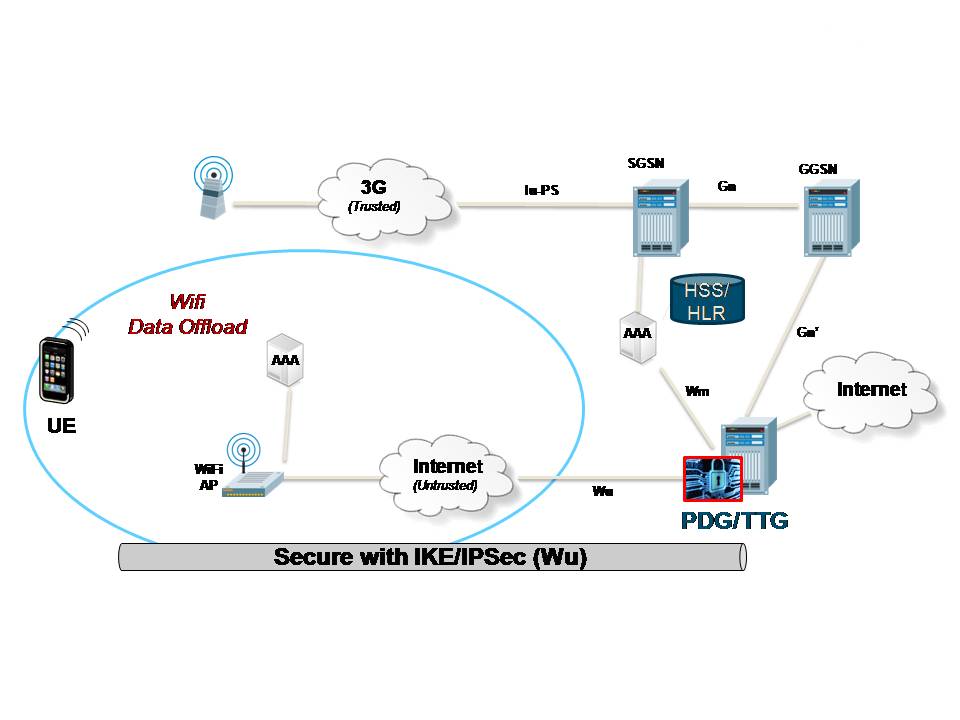
TTG / PDG Configuration for I-WLAN Untrusted Networks
Key Requirements for 3GPP Security Gateways
Mobile operators need highly-scalable and cost-effective security solutions to protect their networks and subscribers as small cells are rolled out in volume in the home, enterprise and wide area public access markets. Carrier-class solutions are preferable to enterprise products, enabling the operator to support potentially large numbers of concurrent, bi-directional IPSec tunnels on a stateful, high-availability system, at the lowest possible cost per subscriber.
Key factors required from a 3GPP SEG to ensure rollout of small cells is accompanied by robust security are:
- carrier-grade availability and redundancy;
- full alignment with 3GPP standards;
- ease of integration into the existing network;
- high scalability and performance
- reuse of the security solution across multiple types of small cells, LTE and macrocells; and
- highly secure hardware and software architecture.
When purchasing a 3GPP SEG, the operator must recognize the location, the performance and the reuse of the software throughout the network. Having the SEG co-located or integrated with the primary elements in the mobile network infrastructure such as the radio network controller, GGSN or PDG is recommended for deployment. Because 3GPP-based public access small cells share many of the same vulnerabilities as closed user group femtocells, reusing the femtocell security architecture is a viable solution. For Wi-Fi small cells, 3GPP’s I-WLAN standard specifies the use of an IPsec tunnel in the end user device as a means of securing what it defines as untrusted Wi-Fi traffic coming into the 3G core.
Jeff Sharpe is senior product line manager for Radisys.
Edited by Stefania Viscusi




