They’re coming at us from all angles.
They want our data, our money, and our intellectual property. They’re taking over our computers and holding them hostage until we pay ransoms.
They’re following our browsing and buying behaviors. They’ve developed the capabilities to listen into conversations at our homes through our smartphones and televisions.
And they can even wrest control of our connected devices – be they baby monitors, TVs, PCs, smartphones, vehicles, drones, surveillance systems, emergency response systems, power grids, or even military arsenals – to spy on or disable us.
Who the “they” are in these scenarios varies based on the situation, of course.
In some cases it’s the guy next door, down the street, or across town. Other hacks involve sophisticated efforts by organized groups. And, increasingly, nation states are involved.
For example, Russia has been in the news a lot lately for its links to the election-time DNC hack. But there’s also been a lot of coverage lately about how the U.S. is or may be leveraging connected technology to further its goals. A recent WikiLeaks report talks about the CIA’s Weeping Angel effort to use smart TVs to listen in on conversations in our homes. And, more recently, media outlets have been running stories questioning whether a hack by the U.S. was responsible for failed missile launch tests in North Korea.
“There is a very strong belief that the U.S. – through cyber methods – has been successful on several occasions in interrupting these sorts of tests and making them fail,” former British Foreign Secretary Malcolm Rifkind told the BBC.
If true, that’s actually encouraging. But most of the discussion around cyber security is deeply disturbing. And, whether hacking efforts are for good or ill, the point is that security breaches are now commonplace.
“From the moment the first worm was unleashed on the internet in 1988, to the massive 2016 Mirai distributed denial of service attack, the cyber security industry has witnessed exponential growth in the volume and variety of cyber threats,” noted McAfee, formerly known as Intel Security.
The Size and Scope of the Threat
The top cyber security threat of 2016 was ransomware, according to the 2017 Annual Threat Report recently released by SonicWall. The network security company said ransomware increased by more than 167 times year-over-year to reach 638 million attacks in 2016.
Ransomware has been extremely problematic this year as well. In fact, as you may recall, a massive attack of this sort in mid-May impacted an estimated 300,000 computers in more than 150 countries.
"This incident exposes how a two-month old vulnerability can cause global panic and paralyze the largest companies and governmental institutions on all continents,” said Ilia Kolochenko, CEO of High-Tech Bridge. “Worse, cybercriminals could have easily released this worm just after the NSA's 0day was leaked two months ago, and this would have led to much more destructive consequences.
“There is nothing new in this particular attack, and the main cause of the epidemic is our failure to adhere to cybersecurity fundamentals,” he added. “Many companies were infected because they failed to maintain a comprehensive inventory of their digital assets, and just forgot to patch some of their systems. Others, omitted or unreasonably delayed security patches. Last, but not least – malware's capacity to self-propagate leveraged the lack of segregation and access control within corporate networks.”
Hardest hit from the global ransomware attack in May was the public health care system in Britain, where hospitals were turning away patients and holding off on surgeries as result. The federal railway system in Germany, FedEx in the U.S., Renault in France, Telefonica in Spain, and Russia’s Interior Ministry were also reportedly victims of this global attack. And although cyber security experts were able to stop the spread of this attack, they warned companies and governments to brace for more to come.
Moshe Ben-Simon, co-founder and vice president of TrapX Security, said the WannaCry ransomware is another example of the accelerating trend of organized crime using ransomware, and that this is happening on three fronts. That includes the deployment of purpose-built ransomware being deployed en masse, such as in the WannaCry attack.
“The second front is for ransomware as a service attacks where organized crime deploys ransomware software products to enable the less skilled criminals to rapidly deploy and clone their own attacks,” Ben-Simon explained. “One recent example of this was the FatBoy RaaS ransomware which has already seen widespread deployment. The third and newest front opened by organized crime in the ransomware war is the idea of selling complete source code for ransomware tools. A recent example of this weaponized ransomware source code, CradleCore, was brought to market by organized crime and has now enabled a broad variety of new attacks.”
Meanwhile, an AppViewX IT Security report lists data leakage as the No. 1 type of hack, with 60.51 percent of the 157 people surveyed at RSA (News - Alert) 2017 choosing that answer. Other top picks were malware and viruses (at 56.05 percent), external hacks (at 55.41 percent), and end user access control (internal) (at 49.68 percent).
The most commonly breached kind of data, according to Forrester, are:
- identities and passwords, at 57 percent;
- customer records, at 49 percent;
- business partner records, at 44 percent;
- employee records, at 41 percent;
- proprietary intellectual property, at 38 percent;
- business partner intellectual property, at 27 percent; and
- non-public financials, at 21 percent.
Meanwhile, Gemalto’s Breach Level Index indicates:
- There were more than a billion data records (1.37 billion) compromised in 2016.
- That means 3,776,738 records were lost or stolen every day.
- Identity theft was the leading type of data breach in 2016, accounting for 59 percent of all data breaches.
- More than 7 billion data records have been exposed since 2013 when the index began benchmarking publicly disclosed data breaches.
“Last year, the account access based attack on AdultFriend Finder exposing 400 million records scored a 10 in terms of severity on the Breach Level Index,” Gemalto reported. “Other notable breaches in 2016 included Fling (BLI: 9.8), Philippines' Commission on Elections (COMELEC) (BLI: 9.8), 17 Media (BLI: 9.7) and Dailymotion (BLI: 9.6). In fact the top 10 breaches in terms of severity accounted for over half of all compromised records. In 2016, Yahoo! reported two major data breaches involving 1.5 billion user accounts, but are not accounted for in the BLI’s 2016 numbers since they occurred in 2013 and 2014.”
Forrester Consulting in a February 2017 white paper says two-thirds of organizations have experienced an average of five or more breaches in the past two years. It adds that hackers compromised more than 1 billion identities last year alone.
And an April story on The Lookout blog said in March of this year alone there were more than 1.45 billion compromised accounts, emails, social security numbers, dates of birth, and other data types.
“Seventeen companies reported data breaches in March, totaling 1,449,373,000 breached accounts,” the blog reports. “Major companies, including Saks Fifth Avenue, Coupa, and McDonald’s (Canada), experienced data loss. However, according to email marketing organization River City Media’s public reports, the organization took the biggest hit with 1.4 billion exposed email addresses. That’s over 96 percent of the total breached accounts for the month.”
We Are the Ones We’ve Been Waiting For
Sometimes our efforts to secure our data, devices, and networks effectively keep bad actors at bay. But efforts to secure our data and systems are not foolproof. So even individuals and organizations that implement security mechanisms sometimes get hacked.
But sometimes security problems occur because we fail to secure our data and things, or do it in a less than optimal way. For example, the River City Media problem reportedly occurred because the email addresses were stored in a database that was improperly secured. Many of us fail to change default passwords on our devices. And sometimes we simply take unnecessary risks with company data and other assets, in some cases because we are not aware of the potential repercussions.
The recent Dell (News - Alert) End-User Security Survey indicates that:
- 72 percent of employees are willing to share sensitive, confidential or regulated company information;
- 35 percent of employees say it’s common to leave a company and take confidential corporate information with them; and
- 45 percent of employees admit to engaging in unsafe behaviors throughout the workday, including connecting to public Wi-Fi to access confidential information (46 percent), using personal email accounts for work (49 percent), or losing a company-issued device (17 percent); and
- 56 percent of employees take on unnecessary risk when storing and sharing their work using public cloud services such as Dropbox, Google Drive, iCloud.
“When security becomes a case-by-case judgment call being made by the individual employee, there is no consistency or efficacy,” said Brett Hansen, vice president of endpoint data security and management at Dell. “These findings suggest employees need to be better educated about data security best practices, and companies must put procedures in place that focus first and foremost on securing data while maintaining productivity.”
How the IoT Expands the Threat Surface
Of course, sometimes security gaps involve devices besides PCs, smartphones, and tablets. And because some devices used in Internet of Things applications are out in the field and not in the hands of users that can quickly recognize when they’re not working as expected, security breaches for them can be especially problematic.
And there are a whole lot of unsecured IoT endpoints out there today. That’s because security wasn’t a concern for their designers, or the suppliers believed that securing them would take more time and money than they thought the market would bear.
But considering that IoT devices are used to monitor and control vital infrastructure like emergency response systems, oil and gas pipelines, power grids, and in life-and-death type of verticals like health care and transportation, security is really an important thing to address.
Nonetheless, the Nokia (News - Alert) malware report revealed mobile device malware infection rates increased steadily in 2016, reaching an all-time high.
According to this report, 2016 saw
- a surge of nearly 400 percent in smartphone malware attacks;
- smartphones as the most-targeted devices in the second half of the year, accounting for 85 percent of all mobile device infections; and
- Android-based endpoints the main targets of such attacks.
“The security of IoT devices has become a major concern,” said Kevin McNamee, head of the Nokia Threat Intelligence Lab. “The Mirai botnet attacks last year demonstrated how thousands of unsecured IoT devices could easily be hijacked to launch crippling DDoS attacks. As the number and types of IoT devices continue to proliferate, the risks will only increase.”
The Corero DDoS Impact Survey 2017 found that the majority (56 percent) of the nearly 100 respondents it polled at RSA 2017 view DDoS attacks as greater and graver concerns in 2017 than in previous years. That’s because DDoS attacks continue to increase in frequency, scale, and sophistication, Corero Network noted.
That’s not surprising in light of the fact that 3.9 billion connected things were in use in 2014, and that’s supposed to reach or exceed 25 billion 2020, Gartner said.
“The Internet of Things is an increasingly attractive early link in attack chains,” said Ray Wagner, managing vice president of the secure business enablement group at Gartner. “By 2020, over 25 percent of identified attacks in enterprises will involve IoT, though IoT will account for less than 10 percent of IT security budgets.”
But Rob Ayoub, research director at IDC, said that organizations for which DDoS protection projects were on the back burner are now re-prioritizing their security strategies to focus heavily on DDoS mitigation.
“As new, large scale attacks have come online leveraging IoT devices, the DDoS threat has become top of mind for CISOs,” Ayoub said. “This shift in precedence puts increased pressure on internet and cloud providers to enable this protection for their customers, and eliminate DDoS threats closer to the source.”
Mobile Malware, Trojans & Phishing Sites
While we’re on the subject of wireless security, here are a few other forecasts and statistics on the security threat to mobile devices:
- The latest mobile threat intelligence report from Skycure suggests 71 percent of mobile devices in the U.S. are highly susceptible to breach.
- Kaspersky Lab’s (News - Alert) mobile malware report for 2016 indicated that mobile malware detections have tripled since 2015.
- The same company reports that the most widespread type of Trojan in 2016 was the advertising variety, accounting for 16 of the top 20 malware programs.
“These Trojans are capable of seizing rooting rights, allowing the malware to not only aggressively display ads on the infected device, often making it impossible to use, but also to secretly install other applications,” explained Kaspersky Lab, which reports indicate could itself pose a security risk for those who work with the Russian company. “These Trojans can also buy apps on Google Play.”
Speaking of things masquerading as other things, the website Bleeping Computer in March reported that global certificate authority Let’s Encrypt in the past year issued 15,270 SSL certificates containing the word PayPal (News - Alert). Of those, more than 96 percent were issued to domains hosting phishing sites.
So that’s yet another threat to consider.
Ilia Kolochenko, CEO of web security company High-Tech Bridge, said this about that revelation: “I think we should separate HTTP traffic encryption and website identity verification questions. Let’s Encrypt’s mission is to globally convert plaintext HTTP traffic to encrypted HTTPS traffic, and they are doing it pretty well. Nonetheless, they should have foreseen massive abuse by phishers, and implement at least some basic security verifications, such as refusing SSL certificates for domains that contain popular brand names inside.”
Investment in Security
Given the current state of affairs around cyber security, it only makes sense that many organizations are increasing their budgets to buy cyber security solutions, implement outsource security services, and invest in training related to security.
In its 2017 Cybersecurity Trends Report, Crowd Research Partners reports that 46 percent of companies are increasing their security budgets by an average of 21 percent this year. Cloud infrastructure, training and education, and mobile devices are getting the most attention on this front, according to the report, which says 33 percent of the spend is going to the cloud, and 23 percent of the spend it going to each of the others areas.
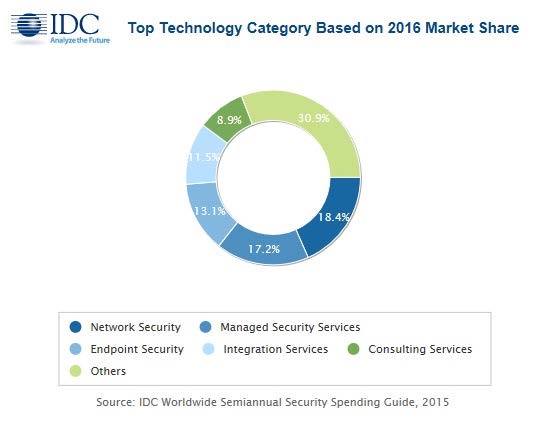
Meanwhile, the Worldwide Semiannual Security Spending Guide from International Data Corp. expects worldwide revenues for security-related hardware, software, and services will reach $81.7 billion this year. That’s an increase of 8.2 percent from last year.
"The rapid growth of digital transformation is putting pressures on companies across all industries to proactively invest in security to protect themselves against known and unknown threats," said Eileen Smith, IDC’s program director for customer insights and analysis. "On a global basis, the banking, discrete manufacturing, and federal/central government industries will spend the most on security hardware, software, and services throughout the 2015-2020 forecast. Combined, these three industries will deliver more than 30 percent of the worldwide total in 2017."
The IDC chart with this story illustrates that nearly of third of the spending will be on consulting services. More than 18 percent will be spent on network security, slightly more than 17 percent will go toward management security services, and about 13 percent will be used for endpoint security efforts.
Edited by Erik Linask




