TMCnet News
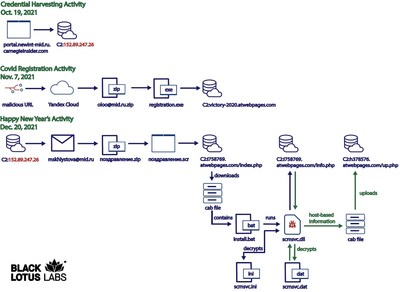
New evidence from Lumen reveals Konni attack on Russia lasted three monthsDENVER, Jan. 6, 2022 /PRNewswire/ -- Researchers at Black Lotus Labs®, the threat intelligence team at Lumen Technologies, discovered new evidence of a months-long campaign against the Russian Ministry of Foreign Affairs (MID). The highly targeted campaign included the deployment of the Konni RAT – a malicious Remote Access Trojan that researchers and governments believe is a tool used by the Democratic People's Republic of Korea (DPRK) since 2014. Black Lotus Labs discovered new evidence of a months-long campaign against the Russian Ministry of Foreign Affairs. "This activity cluster demonstrates the patient and persistent nature of advanced actors who wage multi-phased campaigns against perceived high-value networks," said Mark Dehus, director of threat intelligence at Black Lotus Labs. "If actors attempt to infiltrate the Russian Ministry of Foreign Affairs, what's to stop them from attempting to use these same tactics on other governments or high-profile businesses? For this reason, it is vital for defenders to understand advanced actors' evolving capabilities and tradecraft used to infect coveted targets." Read the full blog here. Timeline of Observed Events The series of persistent actions against Russia's MID occurred from October to December 2021 as follows:
Black Lotus Labs' Response
Additional Resources
About Lumen Technologies Lumen is guided by our belief that humanity is at its best when technology advances the way we live and work. With approximately 450,000 route fiber miles and serving customers in more than 60 countries, we deliver the fastest, most secure platform for applications and data to help businesses, government and communities deliver amazing experiences. Learn more about the Lumen network, edge cloud, security, communication and collaboration solutions and our purpose to further human progress through technology at news.lumen.com/home, LinkedIn: /lumentechnologies, Twitter: @lumentechco, Facebook: /lumentechnologies, Instagram: @lumentechnologies and YouTube: /lumentechnologies. Lumen and Lumen Technologies are registered trademarks.
SOURCE Lumen Black Lotus Labs 
|