
The first thing that pops up in our minds when we talk about containerization is Docker.
The concept of containers eases the development and delivery of distributed applications.
As the saying goes, “With great power comes great responsibility.” Application security is a crucial part of what defines the security of a system. Unaddressed vulnerabilities often lead to undesired consequences, ultimately resulting in the breaking of the application.
In this article, let us go through the security benchmark set for Docker image security, key recommendations, and best practices.
What is Docker Security Benchmark and How Does It Work?
When we say security benchmark, it is essential to note that it is not a tool but a set of guidelines that could be incorporated. The Center for Internet Security (CIS) bases all of its security best practices and guidelines on a consensus-based method, and this is how the Docker Security Benchmark is created.
The process usually starts with identifying the need for security guidance. Once the need or the problem statement is identified, a consensus team is formed that includes subject experts from various fields, including representatives from the industry, the security community, and the government. The assembled team then sets off to gather and analyze the data to get a thorough insight into the current state of the technology, types of attacks performed, and what the current security practices are lacking to mitigate the same.
Based on the data and analysis, the consensus team develops a set of recommendations for securing the technology. The recommendations are designed to be practical, effective, and easy to implement. The final benchmark is released after the feedback has been taken into account. The benchmark is regularly evaluated and updated to keep it up to date with the most recent risks and best practices.
The whole process is rigorous, comprehensive, and data-driven to ensure the highest level of accuracy. The benchmark is built on collaboration and community feedback to make sure it is applicable and helpful for enterprises of all sizes and in all industries.
Key Recommendations from the Docker Security Benchmark
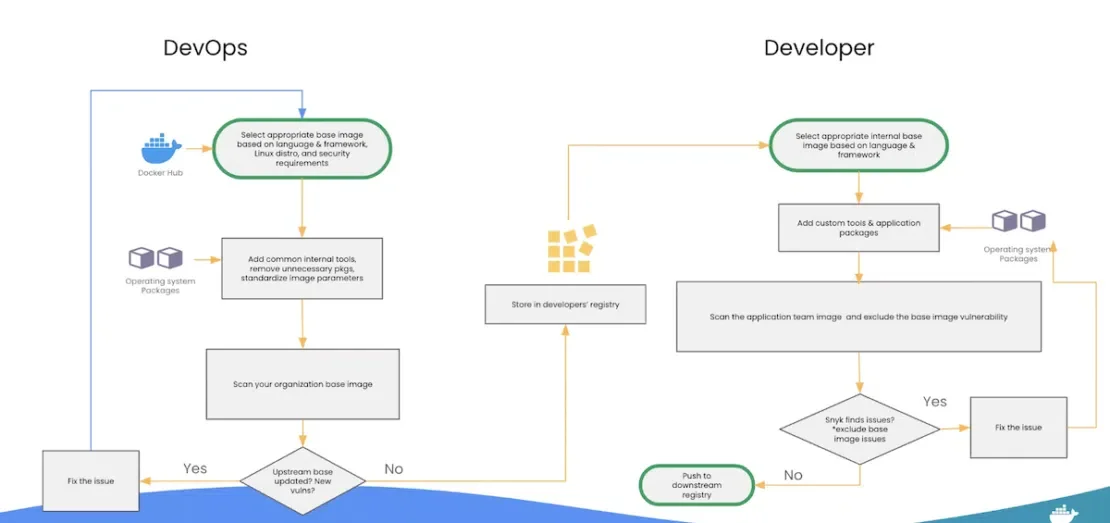
While there are multiple edges in the security infrastructure of any application, at times, it gets daunting to tackle every nuance, and there are always security drawbacks. But, as a rule of thumb, it is always recommended to implement the most common and main security ideas.
The Docker Security Benchmark provides suggestions in a number of key categories, each of which addresses a distinct dimension of securing a Docker deployment.
Host configuration
This concept deals with the hardware and software that operate Docker's host operating system. Recommendations include hardening the system against attack, configuring the kernel, and implementing secure access controls.
Securing container images and build files
Docker image security depends on the aggregated security of the build process and that of the images. Hence, the build process should be secure and trustworthy and should use verified images and scanning tools to find image vulnerabilities.
Docker daemon configuration files
You must secure important data, such as certificates and keys, and make sure that the configuration files are correctly configured and kept up to date.
Securing build pipelines
The benchmark suggests that organizations build containers solely from trusted, confirmed base images and secure the construction process by employing cryptographic image signing and verification. Additionally, it also recommends using a secure CI/CD tool to build and deploy processes and logging build and deploy events for auditing.
Managing secrets
To securely store, manage, and distribute secrets, including credentials, keys, and other sensitive information, the benchmark advises adopting a secret management solution. Additionally, it advises enterprises to cycle secrets regularly and allow only necessary users and processes to access them.
It's crucial to note that many of these suggestions are interconnected and can be used in conjunction with one another. For instance, a good secret management solution can aid in developing pipelines, and a safe CI/CD tool can work with security scanning tools. Additionally, the benchmark advises businesses to adopt a thorough strategy for safeguarding build pipelines and handling confidential information with a focus on continuous integration, continuous delivery, and continuous security.
Best Practices for Docker Security
So, let's get to the most crucial question in this article: What are the best practices for implementing the recommendations of the Docker security benchmark?
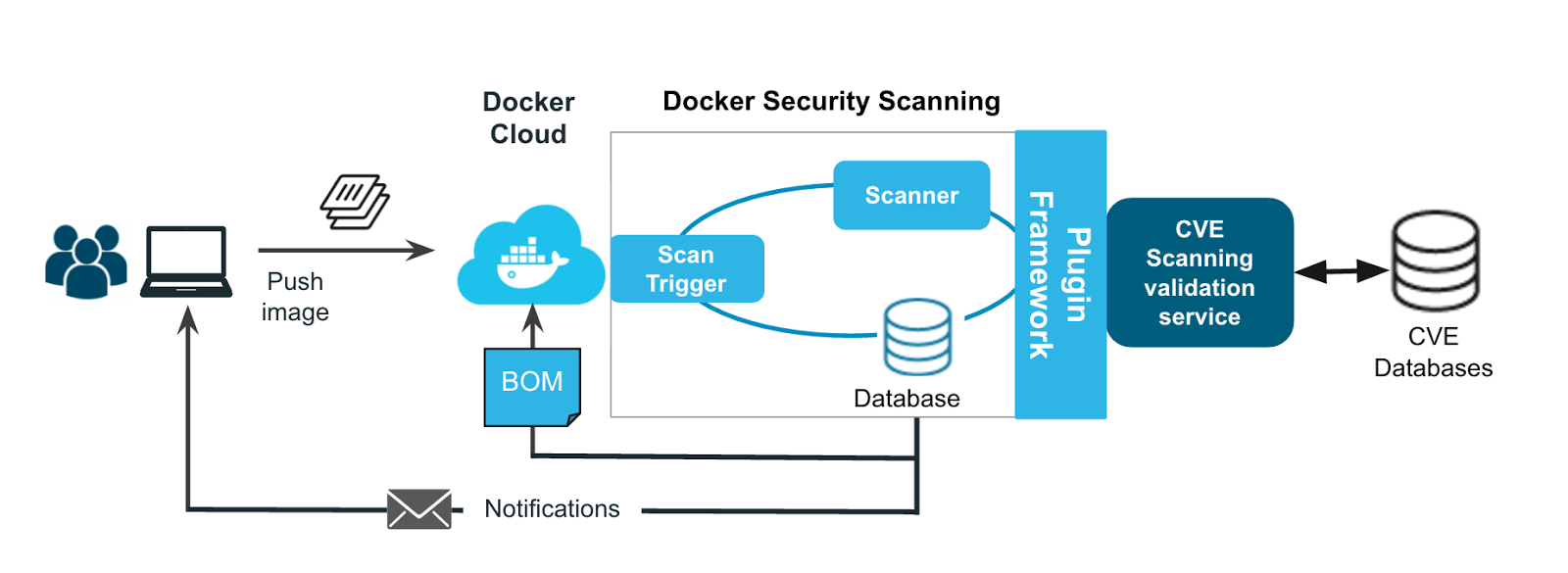
It's essential to remember that your business organization and environment will determine the best strategies for implementing the recommendations into action. However, here are a few general recommended practices for implementing the benchmark's recommendations.
Review the benchmark first
It's imperative to carefully review the benchmark and comprehend the concerns it addresses before you start implementing the recommendations. This will enable you to sort the recommendations according to their importance for your company and its environment.
Conduct a security analysis
Analyze the security of your present Docker deployment to find any vulnerabilities or configuration errors. This will give you a better understanding of your current security posture and serve as a baseline for evaluating how well the benchmark's recommendations are working.
Design a blueprint for security
This is the penultimate step for implementing the security benchmark recommendations. This plan should include guidelines and implementation details to address the crucial risks of the organization. A corresponding timeline for completion should also be included.
Incorporate the recommendations
Start implementing the benchmark's suggestions into practice. Working your way down the list, start with the most critical recommendations. Make sure to test that the recommendations are being applied accurately and as intended.
Perform monitoring and logging
Keep an eye on and manage the security of your Docker deployment at all times. The patching and updating of the images and containers, log monitoring, and routine security scanning are all included in this. To keep your security strategy up to date with the most recent threats and best practices, it's also critical to review and update it frequently.
These are some general best practices that can be implemented in your organization. There can also be some adjustments made to these practices to best suit your requirements and constraints.
Conclusion
Let us quickly review the content covered in the above sections and wrap things up. The Docker security benchmark is a set of guidelines that define how to secure your docker deployment, which includes methods like host configuration, security operations, and building secure pipelines.
These benchmark guidelines are curated after thorough research from field experts and community members backed by data. Ultimately, it is always a good idea to take things with a pinch of salt and implement the benchmark guidelines that align with the requirement of the organization.
