Broadband Internet services and remote access solutions allow today’s information workers to gain full access to IT applications and efficiently conduct business while away from the office. Forward-looking enterprises are investigating ways to extend corporate communications services to Internet workers to further improve employee productivity and reduce telecommunications costs.
Internet telephony enables workers to access corporate voice services over a broadband Internet connection, which means they can conveniently take their office phone numbers and all their corporate voice services with them, wherever they go. Enterprises can leverage Internet telephony to better serve mobile users and teleworkers, as well as to maintain normal business communications during office closings due to weather events, natural disasters or other emergency situations. Furthermore, Internet telephony reduces personal and mobile telephone expenditures by allowing remote workers to leverage enterprise PSTN

facilities for telephone calling.
But connecting enterprise voice and data networks to the public Internet introduces security risks. Enterprises need to protect network resources from malicious attacks, prevent toll fraud, and protect against eavesdropping and identity theft.
Innovative CIOs are looking to next generation Business Communications Platforms (BCPs) to deliver secure Internet Telephony (News - Alert). BCPs extend corporate communications services to Internet users in a secure and reliable manner, without the overhead of special purpose VPN products or other remote access solutions. A BCP can serve as an independent, enterprise-wide voice system serving both Intranet users and Internet users, or it can be deployed to add Internet-facing voice services to an incumbent PBX

.
BCPs Extend Corporate Voice Services to Remote Users
BCPs are specifically designed to deliver reliable Internet telephony capabilities while protecting network resources against abuse and security breaches. Best-of-breed BCPs provide strong user authentication to control access to network resources, encryption capabilities for data confidentiality and integrity, features to protect against malicious attackers and denial of service attempts, plus border traversal capabilities to interwork with corporate NAT

and firewall infrastructures.
User authentication. Strong user authentication techniques ensure that only authorized users gain access to corporate communications services, protecting against toll fraud as well as impersonation. By supporting an incumbent authentication system, such as Microsoft (News - Alert) Active Directory or RADIUS, BCPs deliver single sign-on capabilities and consolidate adds, move, and changes across voice services and other IT services and applications. Leading BCPs support two-factor authentication — requiring users to identify themselves with two unique factors — something they know (such as a password or PIN) and something they have (such as an authenticator device) in order to gain network access.
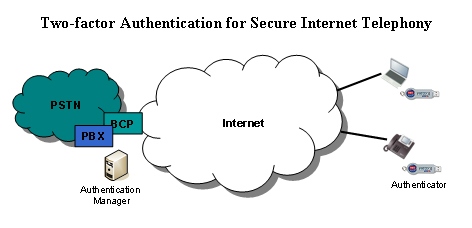 Two-factor authentication is more secure than simple username and password authentication since it requires a user know something, such as a Personal Identification Number (PIN) plus have something in their possession, such as an authenticator. Popular two-factor authentication solutions, such as RSA SecurID support a variety of authenticators including hard tokens, soft tokens, USB tokens and smart cards. Leading BCPs can leverage two-factor authentication solutions to require a user to enter both a PIN and a dynamic token code to gain access to enterprise communications services. Two-factor authentication can be used for softphone clients plus hard phones using IVR token code entry.
Two-factor authentication is more secure than simple username and password authentication since it requires a user know something, such as a Personal Identification Number (PIN) plus have something in their possession, such as an authenticator. Popular two-factor authentication solutions, such as RSA SecurID support a variety of authenticators including hard tokens, soft tokens, USB tokens and smart cards. Leading BCPs can leverage two-factor authentication solutions to require a user to enter both a PIN and a dynamic token code to gain access to enterprise communications services. Two-factor authentication can be used for softphone clients plus hard phones using IVR token code entry.
Data encryption. BCPs are able to encrypt conversation (media) and control (signaling) streams to guarantee VoIP privacy and integrity. Transport Layer Security (TLS) is an industry standard used to encrypt VoIP signaling streams to prevent call hijacking. Secure Real-time Transport Protocol (SRTP) is an industry standard used to encrypt media streams to protect against eavesdropping. By providing standards-based media and signaling encryption, BCPs eliminate the need for special purpose VPN hardware or software for Internet Telephony applications.
Denial of Service (DoS ) protection.
) protection. A malicious attacker may try to prevent legitimate users from accessing network resources and services by overwhelming a VoIP system with service requests. BCPs can identify and protect against DoS attempts by detecting rogue attackers and ignoring packets sent by them.
Border traversal. Enterprises implement NAT and firewall infrastructures at the boundaries of private and public networks to conserve addresses, preserve addressing schemes and protect the private network from the outside world. BCP border traversal features enable VoIP signaling and media streams to traverse these boundaries without introducing security risks, or requiring wholesale configuration changes to the NAT or firewall devices.
Forward-looking CIOs are looking to BCPs to extend their corporate communications services to mobile workers and telecommuters. BCPs enable enterprises to exploit the Internet to increase worker productivity, improve business communications, and reduce telecommunications costs, while protecting corporate voice and data network resources against security threats. The best BCPs eliminate the burden of special-purpose VPN products while delivering advanced security features such as two-factor authentication, encryption, DoS protection, and border traversal capabilities.
Alan Rosenberg is director of Product Line Management for BlueNote Networks (News - Alert). With BlueNote SessionSuite platforms, enterprises, ISVs and partners can quickly and easily embed interactive real-time communication services into a range of commercial or custom software applications, Web sites and internal business processes using industry-standard interfaces and technology. Rosenberg can be reached at [email protected].
Don’t forget to check out TMCnet’s White Paper Library, which provides a selection of in-depth information on relevant topics affecting the IP Communications industry. The library offers white papers, case studies and other documents which are free to registered users. Today’s featured white paper is Best Practices for Implementing a First Contact Resolution Program in the Contact Center brought to you by Enkata.
Communications industry. The library offers white papers, case studies and other documents which are free to registered users. Today’s featured white paper is Best Practices for Implementing a First Contact Resolution Program in the Contact Center brought to you by Enkata.
 Private Branch Exchange (PBX) Private Branch Exchange (PBX) | X |
| Originally, telephone features were provided by telephone central office switching systems, often called CENTREX.�PBX systems emerged as customers wanted to have more calling features and control over...more |
 Network Address Translation (NAT) Network Address Translation (NAT) | X |
| NATs are used to convert private (internal) IP addresses to unique external public (globally-assigned) IP addresses. That is, internal to the company, companies can use ANY IP they want to. The NAT ch...more |
 Denial of service (DoS) Denial of service (DoS) | X |
| Denial of Service begins with a hacker who sends TCP-Transmission Control Protocol SYN-Synchronize message from a friendly site or "spoofed" with internal IP-Internet protocol Address. If target site ...more |
 Internet Protocol (IP) Internet Protocol (IP) | X |
| IP stands for Internet Protocol, a data-networking protocol developed throughout the 1980s. It is the established standard protocol for transmitting and receiving data
in packets over the Internet. I...more |
 Public Switched Telephone Network (PSTN) Public Switched Telephone Network (PSTN) | X |
| A PSTN number is a dialed call which is switched or connected via a CO switching system called a Class 5 End office or in SS7....more |
 Internet Telephony Magazine
Click here to read latest issue
Internet Telephony Magazine
Click here to read latest issue CUSTOMER
CUSTOMER  Cloud Computing Magazine
Click here to read latest issue
Cloud Computing Magazine
Click here to read latest issue IoT EVOLUTION MAGAZINE
IoT EVOLUTION MAGAZINE




