On July 1, in an effort to limit identity theft, data breaches and other cyberattacks that are most often successful due to compromised passwords, Virginia officially became the first state to enact a law focused on digital identities. The new law recognizes the evolving role of digital identity and establishes a legal framework to support the use of stronger third-party credentials in place of weak and vulnerable passwords.
As virtually every business process moves online, knowing who’s on the other end of a transaction becomes increasingly critical, placing digital identity and its associated processes in the spotlight. Moving from account names and passwords to stronger credentials increases online security, but it also adds another dimension of legal complexity, which is exactly what Virginia’s new identity law aims to address. To understand the reasoning and relevance of the new law, let’s explore the basics of both traditional and digital identity, using some well-known scenarios.
There are four high level processes that fall under the identity moniker. The first is to establish an identity by converting select bits of information about a person or thing into a digital record. The next step is to bind a portion of those identity bits to some sort of token that others can trust, also known as a credential. In the third step, authentication happens when a credential is used during a transaction to prove identity. Finally, authorization occurs when successful authentication is combined with additional pieces of information required to approve a given transaction, such as accessing account balance for a debit card transaction.
Everyone is familiar with the Department of Motor Vehicles, and the related process involved in obtaining a new driver’s license or ID card. The reason you are required to appear in person – at least initially – is to establish your identity. When your number is called, and you greet the ultra-friendly and enthusiastic person on the other side of the counter, you must present items such as a birth certificate, social security card, and passport to prove your identity. And, of course, you’ll need to fill out a form.
When your personal information is entered into the DMV computer system, a digital identity is established using the set of freshly verified attributes. Contrast this with the typical process of establishing your identity on a website. In most cases you fill out an online form, select an account name and password, click an email link and voila! You’re done. The difference between the DMV and most online processes is the level of assurance associated with your established digital identity.

When the new license arrives, you now have a credential issued by a trusted authority; your state in this case. Your trusted credential can be presented (in person) to just about anyone, anywhere, as proof (authentication) that you are you. And why? Because people trust the credential and the attributes bound to it; such as name, address, height, weight, age and – best of all – a picture of your face. Your trusted credential is a key to completing many transactions (authorization), including the ability to board a commercial flight. Presenting your license to the TSA agent authenticates your identity and asserts the required attributes to authorize your access to the secured portion of the airport.
The preceding scenario is an example of third-party credentials in the non-digital world. You are the first party, the TSA agent is the second party, and the state DMV is the third party. You endured the process of proving your identity to the state, which, in turn, issued a credential that you presented to the agent who trusts the issuer and accepts the credential.
There’s another highly recognized third-party credential that introduces digital transactions: the payment card. In this scenario, you remain the first party; the merchant or ATM is the second party; and the bank is the third party. The major difference here is that the authentication and authorization processes are now digital. The bank has taken steps to verify your identity and associate the issued debit card (the credential) with your bank or credit account. For a debit card, when you present it to a reader, a PIN must be provided to authenticate. A credit card is very similar, except it can also be used online and over the phone without presenting the actual credential for authentication. In both cases, authorization occurs when the bank verifies account funds or available credit. The payment card industry has spent the last 40 years honing a framework of trust networks, standards and liability agreements between all three parties.
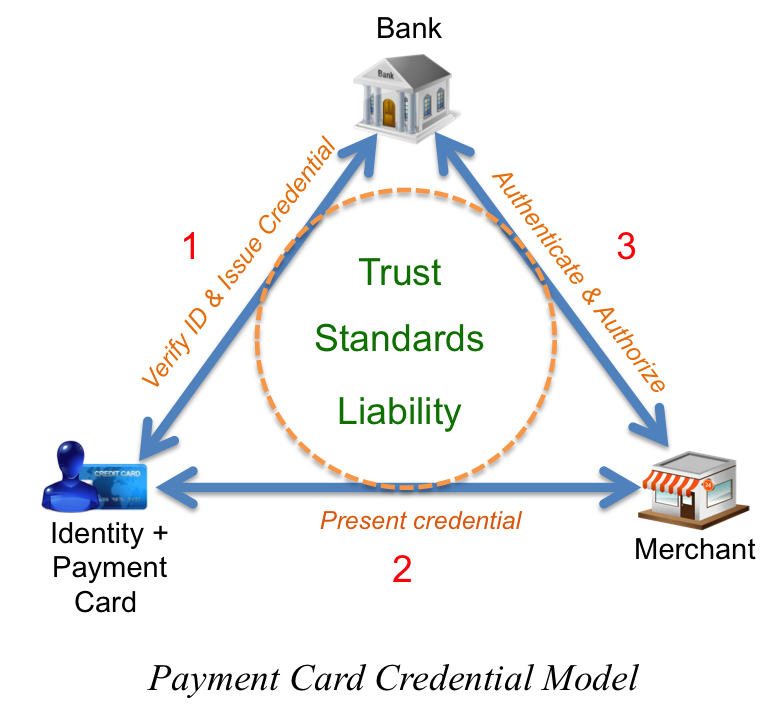
But when a process takes place completely online, the most common tool used to establish identity and perform authentication is the humble keyboard – used to self-assert identity information and type in passwords. There is no common process for obtaining or using a third-party identity credential issued from a trusted source, at least not yet. Further, the establishment of trust frameworks, common standards, and liability management has a ways to go before reaching a maturity level that can support citizen-scale implementation.
Unfortunately, you cannot present your driver’s license or credit card to your computer for authentication. Today’s online transactions take place using a web browser or application that runs on your computer, tablet, or smartphone. To realize the third-party credential vision, users must have a relatively easy way to procure, manage, and present secure digital identity credentials online, instead of using passwords.
Today’s most common form of digital identity credential is the public key infrastructure, or PKI, certificate. These certificates are issued by the third parties referenced in previous scenarios, taking the place of either the state or the bank. Companies that issue and manage these credentials are commonly known as credential service providers, or CSPs.
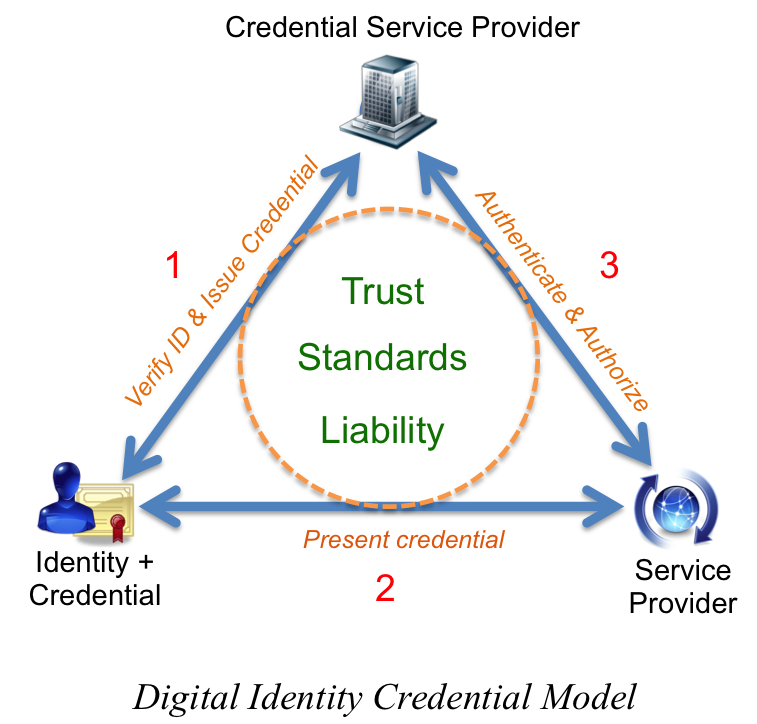
Interestingly, CSPs have built most of their business around issuing digital identity credentials to web servers. Website owners go through a similar process to establish the identity of a website to obtain a credential (certificate) that is loaded onto a server. Whenever you navigate to a website using https, and/or see the little padlock in your browser window, you’re seeing the result of an authenticated and authorized digital identity credential.
These same credentials can be issued to people, using a very similar process; just ask Uncle Sam. For more than a decade, the U.S. government has been transferring high assurance identity proofing to a set of PKI digital identity credentials that are securely encoded on a smart card. But these credentials are only issued to federal employees and contractors, and only used within the U.S. federal ecosystem. So what about everyone else?
In 2011, the White House released the National Strategy for Trusted Identities in Cyberspace, which “charts a course for the public and private sectors to collaborate to raise the level of trust associated with the identities of individuals, organizations, networks, services, and devices involved in online transactions.” In short, the idea is to encourage industry to work out a common set of business, legal, and technical frameworks that will encourage widespread adoption of secure credentials by all three parties.
Third-party credential systems have been part of our collective identity ecosystem since far before the dawn of cyberspace. Virginia’s identity law is a positive, yet small step toward realizing an effective third-party digital identity credential system by solidifying (at least for Virginia) predictable liability and common standards. But the law alone is not enough. To realize the full vision, citizens need to move away from passwords in favor stronger credentials. Online service providers also need to utilize technologies that can digitally accept and verify said credentials with the third-party provider. Only time will tell how long it will take for all the pieces to come together. In the meantime, the humble keyboard continues to broker the ever-feeble password.
Ashley Stevenson is the identity technology director at ForgeRock (www.forgerock.com).
Edited by Kyle Piscioniere




