|
A s service providers rapidly roll out VoIP services and VoIP technology continues to evolve, law enforcement agencies face new challenges in trying to understand these changes and determine how to gain access to the communication exchanges occurring over these new services. At the same time service providers — both broadband access providers and VoIP service providers — need to keep up with changing standards, the changing needs of law enforcement agencies and the rapidly changing VoIP offerings and technologies. Certainly, service providers realize the importance of lawful intercept (LI) and do their part in meeting their requirements, but they typically have limited experience in lawful intercept and are looking to solutions providers to help them architect and implement solutions that meet their requirements and legal obligations. A History Lesson
Some of the early adopters and implementers of the VoIP concept were North American cable companies. These cable operators were looking for additional income sources outside of TV, and looked to both the burgeoning ISP environment, as well as the capability to use their IP capability to go after the huge telecommunications market. Cable companies already had vast networks connecting into most households, but didn’t have significant internal connectivity or “backbones” for transporting, switching, and connecting phone calls like the incumbent, traditional phone companies. It turned out that the highly decentralized, smaller, cheaper VoIP phone switches and gateways were exactly what they needed. Cable companies could cost-effectively deploy phone services one market at a time and grow the solutions as needed. As a result, CableLabs, the cable industry’s self-sponsored technology development body, was the first industry group to come up with a methodology for performing Lawful Intercept in a VoIP environment.
Later, a second standard (T1.678) emerged for the non-cable (primarily DSL) providers. The creation of a second standard should not be a surprise considering the primary providers of DSL were the traditional phone companies that were then competing with the cable operators.
Recently, new “service only” companies (e.g.,
Vonage (News - Alert)
have emerged (like the ISPs in the past) to take advantage of the abundant supply of broadband access (cable or DSL) available to residential subscribers from various broadband providers. They have leveraged this access, successfully competing with the broadband access providers to carve out their own share of the big telecom pie.
It’s all about Technique
Given the differences in the architectures used by these various service providers, several different techniques have been developed to implement lawful intercept in their networks. The one that has the most history and practical implementation experience is an interface that works directly with the existing switching devices (CSCF, call agent, softswitch) and the edge devices (SBCs, BRAs, CMTs, gateways, DSLAMs, etc.) that the service provider already owns and operates.
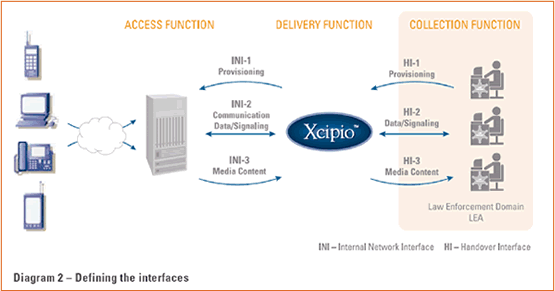
(Editor’s Note: Diagram #1 accompanying this article shows the overall Lawful Intercept (LI) architecture, Diagram #2 defines the interfaces.)
These direct interfaces between the delivery function and the network elements both provision them (via TCP/IP) and receive data/content from them. This creates a very complete and reliable LI solution that handles various call-flows in the network while delivering the intercepted traffic to law enforcement via a documented and proven methodology.
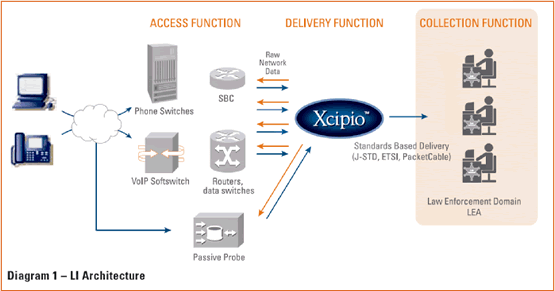 |
These interfaces are described as Internal Network Interfaces (INI). INI-1 is for provisioning network elements, INI-2 receives call data and signaling messages (off hook, dialed digits, ring back, hook flash, etc.) from the network elements and INI-3 connects to the edge devices to receive a copy of the media stream. All of this information is sent to the delivery function from the various network elements. The delivery function then sorts, filters, and formats the information for delivery to law enforcement.
The interfaces used to deliver the call data events and media content to Law Enforcement are called the Handover Interfaces (HI) and are defined as follows: HI-1 is the interface by which the warrant is faxed to the carrier for provisioning in the Delivery Function. HI-2 and HI-3 utilize TCP/IP connections and transport, respectively, call data and media content. These interfaces comply with standards such as PacketCable and T1.678 for delivery of intercepted traffic to law enforcement.
The solution described above is categorized as an active solution since it actively communicates with the devices in the network and receives information from them.
An alternate to an active solution is a passive solution, in which the INI-1, INI-2 and INI-3 interfaces still exist, but they are redirected to probes placed strategically in the network. These probes search for information relevant to the target, replicate it, and send it back to the delivery function for processing. The same HI-2 and HI-3 interfaces and standards are used by the delivery function to deliver the information to law enforcement for both active and passive solutions.
 |
The Broadband Access Environment
In contrast to a service provider that provides VoIP, in a broadband access (DSL, cable, and fiber) environment, the operator doesn’t know what services the subscriber is utilizing because operators only supply a “pipe” from the subscribers’ premises to the Internet. In this case, the service provider doesn’t provide any “switching” equipment and the subscriber can work with any service provider (e.g., Vonage) they choose via the “pipe” to the Internet. The subscriber can also decide to use peer-to-peer services (e.g.,
Skype ( News - Alert)
over this same broadband “pipe”.
In this environment there are still active and passive solutions, but the difference is in the inability to identify or determine certain events or information due to the service provider not owning or controlling the switching and routing equipment. A solution in this environment would typically only utilize INI-1 (provisioning) and INI-3 (media content) interfaces. For either active or passive solutions, INI-1 would be used to pass a target identifier such as an IP address (or possibly a MAC address, email address, chat ID, etc.) and the device (router, switch, probe) would replicate all traffic going to/from that target and send it to the delivery function via the INI-3 interface. Once the delivery function receives the information, certain content can be separated based on port/protocol type. This means that RTP (voice) and email traffic, SIP messages, Skype traffic, etc., could be separated, processed, and delivered to law enforcement separately according to the delivery standard in place. Separating the content over the pipe, however, does not mean that encrypted traffic would be decrypted by the delivery function.
Meeting Law Enforcement Expectations
For service providers who actually own the service and employ a centralized call control architecture, law enforcement expects that they will be able to provide full LI capability because they own both the switching equipment and the applications. Typically, these types of providers have the capability and responsibility to deliver call data events and media content (HI-2 and HI-3) per the appropriate LI delivery standard.
Conversely, for service providers merely providing broadband access (DSL, cable, and fiber) and are not providing any telephony switching or communications applications (e.g., Skype or other IM), law enforcement expects to receive the whole “pipe” of information going to/from the subscriber. This is because the service provider has no knowledge or control over the content. In some cases, the delivery function is able to separate some protocols or types of data, but true analysis and decryption requires law enforcement to utilize the various tools and techniques available to them.
The capability and responsibility for these broadband service providers really amounts to providing the media content (HI-3) according to the relevant delivery standard. Other event-based information may be available and distinguishable so that it can be delivered over HI-2, but that will depend heavily on the types of services and protocols in use by the subscriber.
Despite the hype about the challenges facing providers in achieving compliance, some areas of VoIP have lawful intercept techniques that are well defined and established. In other areas, techniques and delivery standards are fairly new. To determine if the hype surrounding this issue has merit, a comparison can be made to the wireless data industry. Lawful intercept for wireless data has been around since its inception but has not put any undue burdens on that technology. In fact, it has been both widely adopted and wildly successful. With this in mind, there is very little reason to think that including a well-architected and thought-out solution for the lawful intercept of VoIP services will prevent continued innovation and worldwide adoption of that technology. 
Scott Coleman is Director of Marketing at SS8 Networks in San Jose, California, where he educates, evangelizes and raises general awareness of Lawful Intercept solutions and capabilities. For more information, please visit the company online at www.ss8.com.
|

